Edge Cybersecurity in Railway
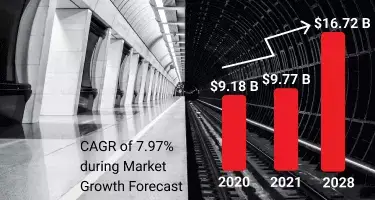
According to Fortune Business Insights,
“Railway Cyber Security Market Size, Growth and Report [2028],”
the global railway cyber security market stood at $9.18 billion in 2020. In that same report, it’s also estimated the market was projected to reach $9.77 billion in 2021 and grow to $16.72 billion by 2028 with a CAGR of 7.97% during the 2021-2028 period.
In a world that is increasingly connected and digital, cybersecurity is no longer an operational requirement, it’s an economic necessity that is vital to the continued health of an industry that is in dire need of modernization.
There are three key aspects of the railway system: the command and control systems which deal with safety and signaling, rail traffic and operations which helps keep trains on schedule, and the corporate side of the business which oversees the system’s interaction with customers.

Real-time data sharing offers substantial gains for passengers, operators, regulators, and OEMs, including the ability to keep schedules, operate cost-effectively, and offer competitive transportation services. Real-time data helps railways gain abilities and automation to streamline passenger flow, identify and mitigate risks, and optimize energy consumption to reduce emissions.
Edge and artificial intelligence are powering railway modernization and re-shaping its future by identifying improvement areas, automating routine tasks, enhancing communication systems, tracking specific parameters, creating new rules, and more.
With so much data being generated at the Edge, the real challenge lies in securing it against threats and attacks.
Edge Security Risk Use Cases in Railway
Secure Railway Edge/IoT environment
As security concerns continue to ramp up in the railway industry, the need for end-to-end security is reaching a critical point. Railway systems need to have smart solutions embedded to discern threats from non-threats, with remediation actions to keep them at bay.
Edge helps overcome latency and bandwidth challenges, moving data and providing a reliable system operation, but inevitably, it also comes with many vulnerabilities that cyber criminals exploit to attack the Edge.
Cybersecurity processes need to start with a risk analysis to know what’s inside your equipment and what role it plays in your system. Areas like power control, level crossing automation, and signaling systems are essential, meaning you need to accurately detect and reduce vulnerabilities as they can destroy digital assets, compromise the system, or result in the loss of information.
Data transfer protection in real-time
Data collection and real-time information help power decision-making and provide customers with useful and up-to-date information. Big data covering millions of customer journeys can also be used for purposes such as transport and infrastructure planning.
The industry is exploring novel methods of obtaining and analyzing passenger data and train operations, for example on-train sensors, trackside signals, and smart ticketing apps. Onboard computers collect, process, and store device data locally. Said data is transferred in near-life mode over 4G or 5G connections as the train is moving, with some portions of the data retrieved via Wi-Fi and others transmitted to the cloud.
Usually, train systems are encrypted with mutual TLS or VPNs, but this architecture is also prone to brute force attacks, DDoS attacks, or scanning vulnerabilities.
The security landscape is constantly changing, with more complicated attacks being developed all the time and it is imperative that the rail industry keeps pace with these developments to protect their data and critical infrastructure.
The more the industry relies on digitisation, the bigger the possibility of attack and the higher the risk to passenger safety and security of rail assets. Breakdowns, signal failures, software failures, and passenger data breaches are all potential consequences of a cyber-attack, let alone the possible reputational and financial damage.
How AI EdgeLabs Can Strengthen Cybersecurity in Railway
Through digitalization, railroads are now able to drastically improve their maintenance processes.
Currently, an increasing number of businesses rely on the following technologies: Industry 4.0, which includes the Industrial Internet of Things (IIoT), edge computing, big data, analytics, and cloud computing, allows maintenance agents to gather real-time status information about onboard equipment, while also introducing new approaches to flexible production, preventive and predictive maintenance, and remote quality control for rolling stock.
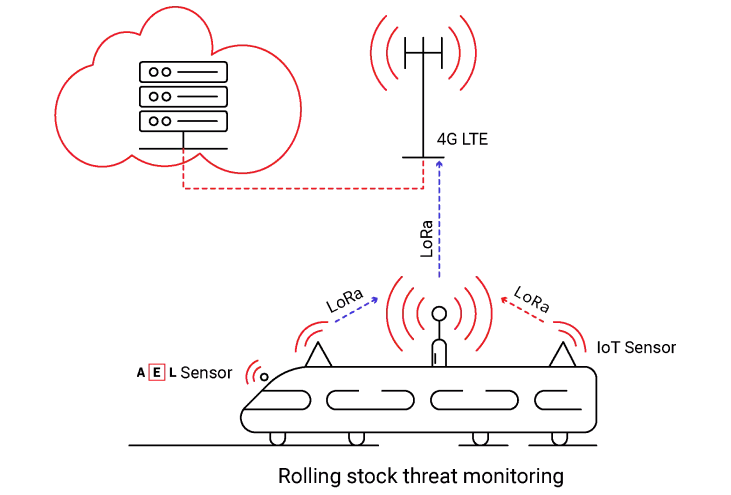
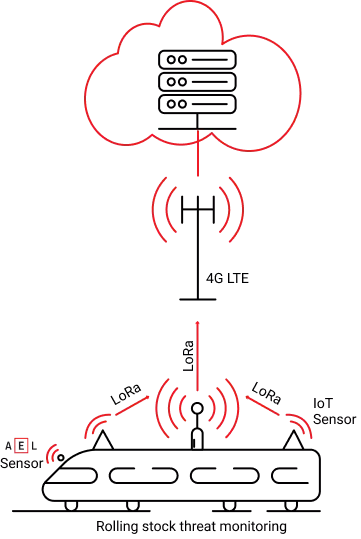
When it comes to rolling stock equipment and monitoring, Edge servers that are connected to 5G/4G or even Wi-Fi networks are present on board the train.
Possible deployment examples
Through digitalization, railroads are now able to drastically improve their maintenance processes.
Currently, an increasing number of businesses rely on the following technologies: Industry 4.0, which includes the Industrial Internet of Things (IIoT), edge computing, big data, analytics, and cloud computing, allows maintenance agents to gather real-time status information about onboard equipment, while also introducing new approaches to flexible production, preventive and predictive maintenance, and remote quality control for rolling stock.
When it comes to rolling stock equipment and monitoring, Edge servers that are connected to 5G/4G or even Wi-Fi networks are present on board the train.
Thanks to our lightweight agent deployed on-premises and able to cope with unstable connectivity or offline operations, we provide asset visibility and discovery in OT/IT environments. AI EdgeLabs offers network data analysis in real-time as well as remediation by preserving low latency.
Our mix of reinforcement learning and machine learning algorithms, our edge security platform protects your edge and OT/IT environments from network threats and zero-day attacks with up to 99% accuracy.
AI EdgeLabs is a robust, enterprise-grade, and AI-based platform that brings advanced network visibility, early threat detection, and automated incident response and remediation vital for the railway industry. Enriched with Deep Reinforcement Learning, our platform is smart and impressively accurate in detecting threats before they even have a chance to cause harm.






