Edge Cybersecurity in Telecommunications
Efficient’s
“Global DNS Threat Survey Report”
found that telecommunications companies suffer more attacks than any other industry surveyed, with most admitting they have faced four attacks on average on a yearly basis. The cost for a breach in telecommunication companies can also be higher, with the damage averaging at $600,000 in the sector. Furthermore, 5% of respondents admitted to an attack that surpassed $4.95 million.
The ongoing and steadily increasing growth of internet traffic, accelerated by Edge computing, artificial intelligence, and mobile app usage, to name a few, has triggered a significant rise in cybersecurity threats for the telecommunications industry.
As the world takes concrete steps to move to 5G networks, there’s a constant push for telecommunication companies to strengthen their security if they are poised to make that leap towards true digital advancement and transformation.


In comparison to other industries, telecommunication companies have by design the biggest active server infrastructure, actively making it more vulnerable than any other industry out there.
Edge Risk Use Cases in Telecommunications
Patching and DNS Attacks
Telecommunication companies are susceptible to zero-day attacks, which make patching incredibly powerful and effective. Poor response to DNS attacks is also easy to exploit by bad actors who know this is one of the longest risks to mitigate. According to Efficient’s report, 55% of businesses need at least an entire business day or more to mitigate a DNS attack.
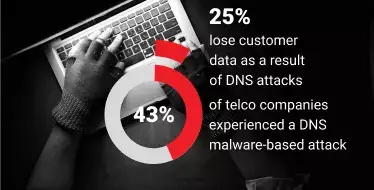
Also, 43% of telecommunications companies experienced a DNS malware-based attack because they were lax in applying critical and necessary patches that were particularly created to mitigate those threats. Surveyed telecommunications companies admitted they are losing customer data as a result of a DNS attack in 25% of cases.

DDoS attacks
In the first quarter of 2021, the telecommunications industry was the
most targeted sector for distributed denial of service (DDoS) attacks.
The malicious attack floods the traffic of a targeted server or network with an army of bots that can either completely shut down a service, damage the server infrastructure, disrupt day-to-day operations, among many other technical and damaging issues.
There are instances where DDoS attacks are used to weaken security measures like firewalls to focus their attention on something other than a larger-scale attack that may be taking place simultaneously.
Severe DDoS attacks can result in weeks of downtime, which can cause telecommunications providers to lose millions if not billions of dollars in losses as well as in brand reputation. Some risk mitigation strategies against DDoS attacks include web app firewall technology, content distribution networks, or the rerouting of DDoS-generated traffic through a filter that removes malicious traffic and only allows normal traffic to move ahead.
DDoS attacks remain a serious threat to telecom providers around the world as attackers discover even more ways of boosting the power and scale of attacks. Another trend observed during these years was the use of vulnerable IoT devices in botnets to launch DDoS attacks.


The impact of a DDoS attack should not be underestimated. Direct attacks can reduce network capacity, degrade performance, increase traffic exchange costs, disrupt service availability and even bring down Internet access if ISPs are affected. With a growing number of connected devices and systems supporting mission-critical applications in areas such as healthcare and transport, unexpected downtime could be life threatening.
The Internet and telecom sector is among the industries that experienced
the biggest spike in DDoS attacks in 2020,
a 210% increase over 2019. For the first time in history, the annual number of DDoS attacks crossed the 10 million threshold in 2020 and regionally, the attack frequency in EMEA in the same year was 3.71 million, with a peak volume of 586 Gbps and 7-day peak duration.
Session Initiation Protocol (SIP)
Usually paired with voice-over-IP (VoIP), SIP represents a prime target for telecommunications attackers who prey on exposed networks to exploit vulnerabilities. With the rise of remote workers reaching sky-high numbers, there are more SIP endpoints than ever before to support entire legions of remote workers, and as such, criminals use this medium to steal identities, inject malware and viruses, perform fraud, hijack a system, or eavesdrop to steal information.
Real-time signaling analysis is one of the most effective ways to protect telecommunications companies against SIP-targeted attacks.
5G Threats
5G increases the total surface area for malicious attacks on the telecommunications industry, and according to the 2021 Department of Defense guide called
“Potential Threat Vectors to 5G Infrastructure”,
the most pressing threats when rolling out or providing 5G services include:
Software configuration management: Hackers can modify software or network components to weaken security measures, install viruses, or gain unauthorized access with admin permission.
Network security: Attackers target connectivity between mobile devices and small cell towers to intercept, alter, or destroy critical data operations.
Spectrum sharing: Telecommunications providers of 5G services use high and low spectrum frequencies, giving attackers access to interrupt critical information pathways.
Network slicing: Slicing 5G networks in multiple sections increases infrastructure complexity, giving hackers room to target and access data from specific slices.
Software Defined Networking (SDN): SDN easily re-configures network routes which hackers can tamper with to embed code that reduces performance and limits bandwidth.
How AI EdgeLabs Can Strengthen Cybersecurity in Telecommunications
Attacks on a telecommunications company's infrastructure can lead to far-reaching consequences that can potentially impact businesses, consumers, government agencies, and entire nations.
Even though the telecommunications industry is considered more mature in terms of cybersecurity strategies than other industries like manufacturing, there is still a distinctive and critical need to strengthen cybersecurity initiatives, governance, resiliency, risk management, and threat remediation with a holistic approach that protects against existing, new, and sophisticated forms of attack.
AI EdgeLabs is a robust, enterprise-grade, and AI-based platform that brings advanced network visibility, early threat detection, and automated incident response and remediation vital for the newest technologies for the telecommunications industry.
The AI EdgeLabs Sensor is a proprietary network telemetry and monitoring agent that continuously scans and reports network and Edge/IoT Gateway performance and configuration.
The AI EdgeLabs Sensor helps:
- Generate near-time visibility of infrastructure and application performance.
- Prevent and block threat sources in real-time.
- Integrate cloud-based and on-premises application performance monitoring.
- Monitor SaaS applications from your users’ vantage point.
The User Plane Function (UPF) is a fundamental component of a 3GPP 5G core infrastructure system architecture. The UPF represents the data plane evolution of a Control and User Plane Separation (CUPS) strategy, first introduced as an extension to existing Evolved Packet Cores (EPCs) by the 3GPP in their Release 14 specifications. CUPS decouples Packet Gateway (PGW) control and user plane functions, enabling the data forwarding component (PGW-U) to be decentralized. This allows packet processing and traffic aggregation to be performed closer to the network edge, increasing bandwidth efficiencies while reducing network.
Committing to a complete implementation of control and user plane separation, however, is a complex proposition which only provides a subset of the advantages adopting a 5G User Plane Function affords, such as network slicing. Deployed within a dynamic cloud native compute infrastructure, the User Plane Function delivers the packet processing foundation for Service Based Architectures (SBAs).
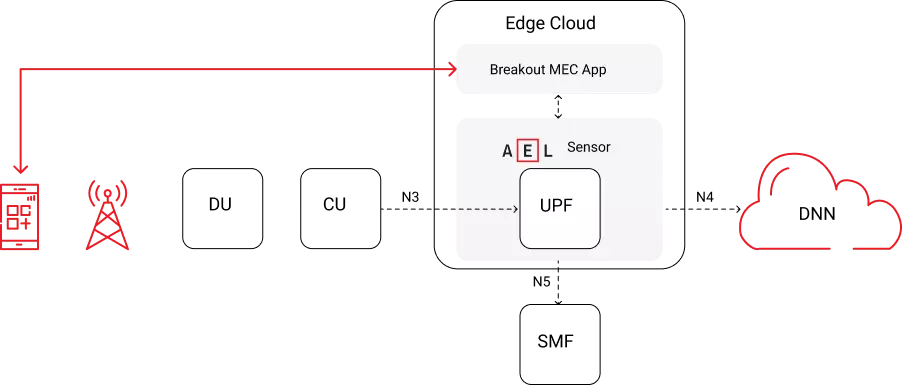
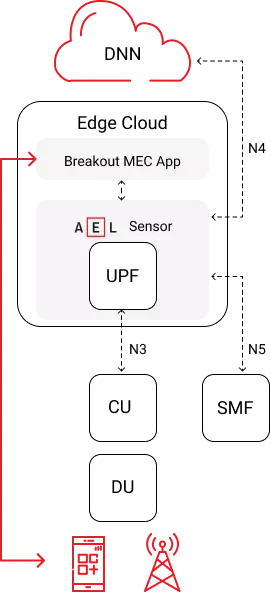
In Local Breakout mode, AI EdgeLabs can operate behind UPF to guarantee traffic quality to provide threat prevention. In breakout mode, all session connectivity data is redirected as depicted in the following figure.
Possible deployment examples
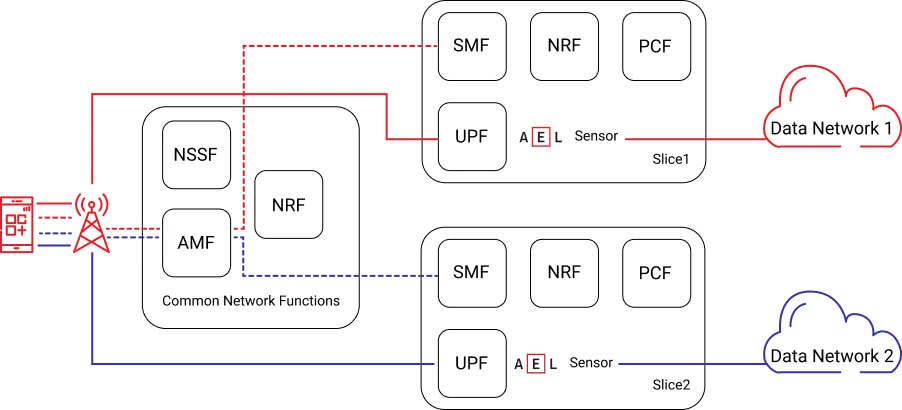
The concept of network slicing is illustrated via multiple logical UPF slice instances, whereby each slice may represent specific, differentiated network capabilities and network characteristics as seen further below in figure.
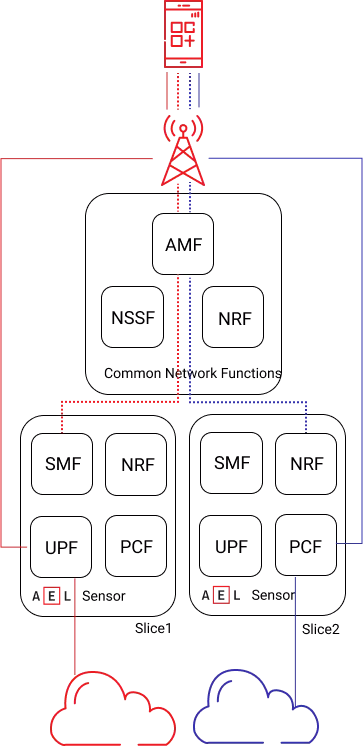
AI EdgeLabs is the UPF Optimized for container-based Network IDR Fully, multi vendor solution.
AI EdgeLabs is a robust, enterprise-grade, and AI-based platform that brings advanced network visibility, early threat detection, and automated incident response and remediation vital for the telecommunications industry. Enriched with Deep Reinforcement Learning, our platform is smart and impressively accurate in detecting threats before they even have a chance to cause harm.






