The SSH-Snake attack is particularly alarming due to its innovative approach to network infiltration and expansion. Unlike traditional malware, SSH-Snake is a self-modifying worm that operates in a fileless manner, making it extremely difficult to detect and eradicate. This advanced threat leverages SSH credentials found on compromised systems, using them to propagate across networks and execute lateral movements with an efficiency and stealth previously unseen.
SSH-Snake: What Is It
SSH-Snake is an open-source penetration tool unleashed on January 4, 2024 on Github by security engineer Joshua Rodgers. Originally designed to perform automatic network traversal using SSH private keys discovered on systems, as well as visually map the SSH connections throughout a network, it is being actively used by threat actors for malicious purposes.
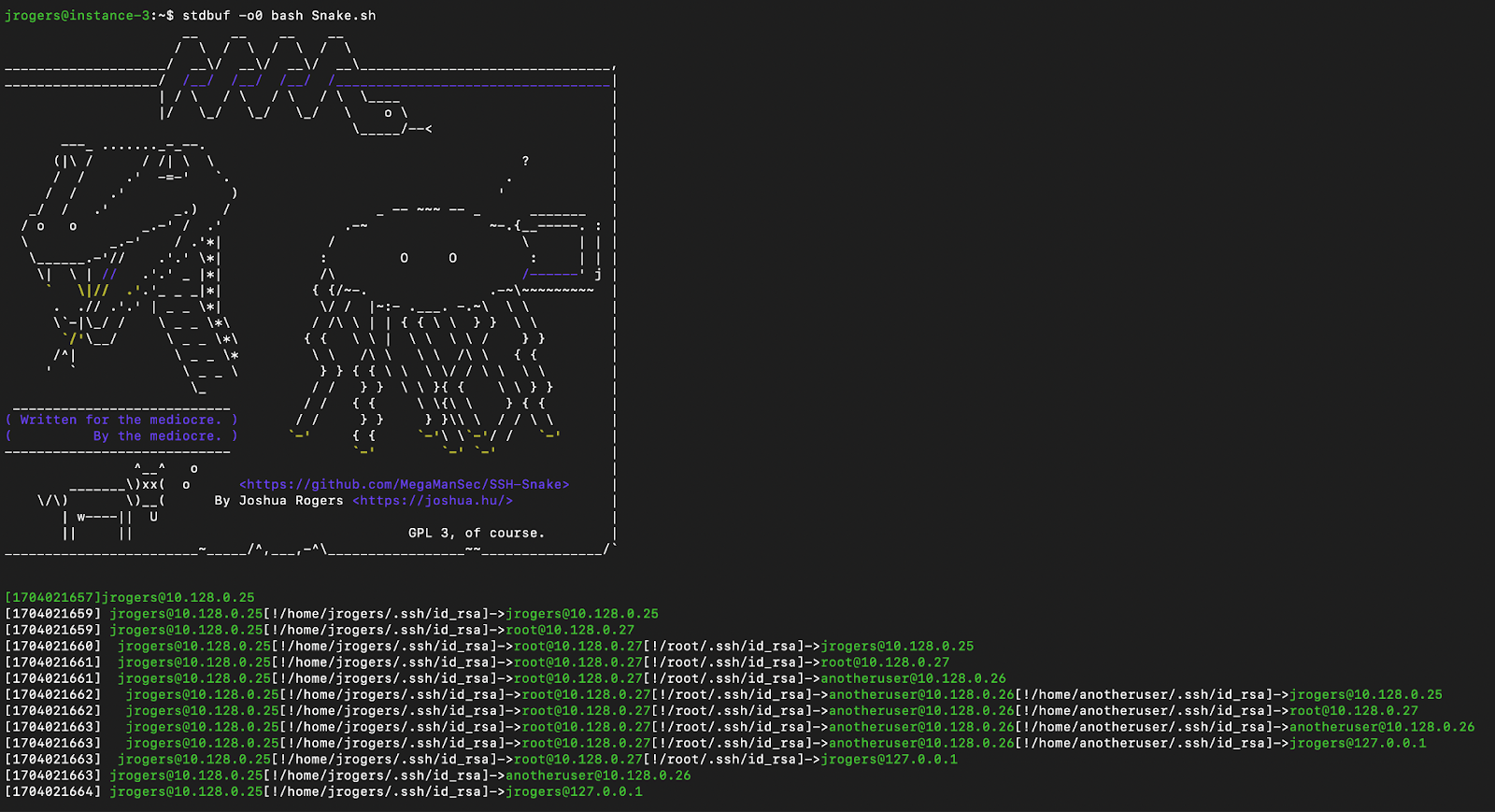
SSH-Snake is a cunning, self-modifying worm that exploits SSH credentials to spread its venomous presence across networks. Like a stealthy serpent, it autonomously hunts down compromised systems, extracting SSH credentials, and using them to proliferate its malicious payload.
Uniqueness and Functionality of SSH-Snake Worm
Unlike anything encountered before, SSH-Snake boasts a groundbreaking feature: self-modification upon its initial execution. It dynamically reshapes itself, shedding excess baggage to operate with maximum efficiency. By stripping away comments, whitespace, and superfluous functions, SSH-Snake emerges as a lean, mean hacking machine, ready to infiltrate even the most fortified networks. Its self-replicating, fileless nature ensures a seamless integration into any environment, making its detection by traditional signature-based solutions impossible.
In comparison with traditional worms, SSH-Snake transcends device limitations, effortlessly penetrating any system in its path.
Being a bash shell script, SSH-snake autonomously hunts for SSH credentials on the host system. Once credentials are found, the script attempts to log into the target system and then copies itself there in order to repeat the process on other machines.
Here are all the automated tasks that the SSH-Snake performs:
- Exploring standard repositories like .ssh directories and configuration files for commonly stored SSH keys and credentials.
- Scanning shell history files (.bash_history, .zsh_history) to detect commands (ssh, scp, rsync) linked to SSH private keys.
- Leveraging the 'find_from_bash_history' functionality to scrutinize bash history for SSH-related commands, revealing explicit mentions of private keys and associated credentials.
- Examining system logs and network caches (ARP tables) to identify potential targets and collect data facilitating the discovery of private keys.
AI EdgeLabs Detection & Response Capabilities
To detect signs of the SSH-snake worm, AI EdgeLabs utilizes a rule called "Read SSH Information" by leveraging the Falco framework.
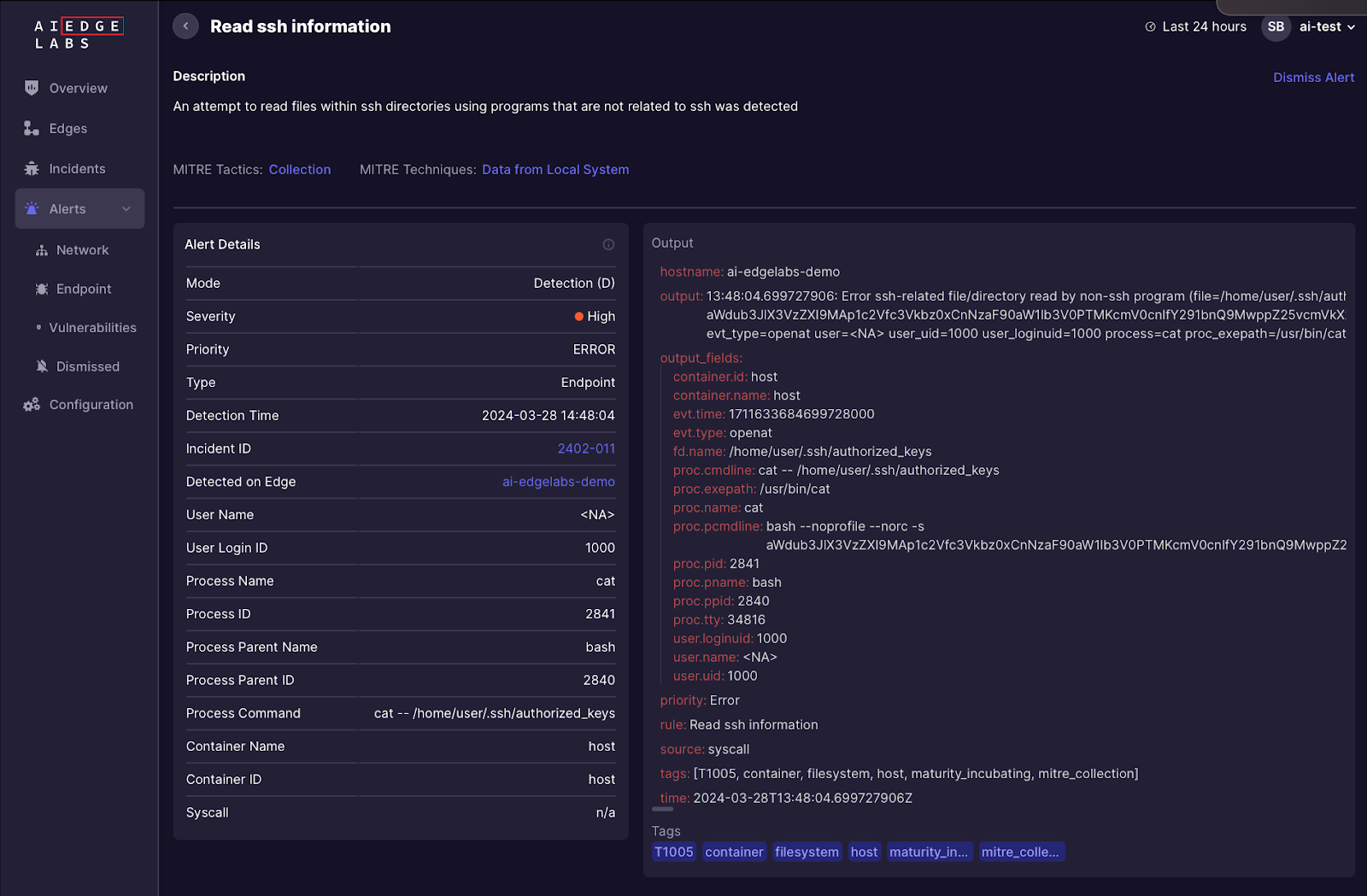
This rule indicates attempts to access files within SSH-related directories. Nevertheless, the Falco framework alone lacks the precision needed for effective SSH-Snake detection, as it can potentially flag legitimate activities and necessitates meticulous refinement, considering the intricacies of the infrastructure.
AI EdgeLabs has enhanced SSH-Snake worm detection by implementing a new detection mechanism, consisting of the following stages:
- Process ‘find’ looks for private credentials in directories that contains .ssh
- Process ‘grep’ and proc.exeline contains "ssh|scp|rsync" and fd.filename = .bash_history
- The attempt to read a non-existent file when executing a script encoded in base64 over ssh.
AI EdgeLabs not only has the ability to detect but also to proactively respond to the SSH-Snake worm by utilizing our own SSH-Snake response mechanism, which allows you to instantly remove the SSH-Snake and stop its spread.
Response consists of 2 stages:
- Stopping current execution
- Preventing reinfection
Upon detection of malicious code being executed, our solution can quickly identify the IP address of this connection and terminate it, along with terminating all child processes run by the SSH-Snake worm without affecting production services. Simultaneously, the malicious IP is added to the blocklist, aiding in preventing the spread of malicious activity.
Proactive Network Security: Defending Against SSH-Snake's Stealthy Threat with AI EdgeLabs
SSH-Snake's effectiveness and the difficulty in detecting its presence underscore the necessity for organizations to employ runtime threat detection tools and to adopt a proactive stance towards network security. The emergence of SSH-Snake highlights the continuous evolution of cybersecurity threats and the need for innovative defenses to protect against increasingly sophisticated attacks. SSH-Snake's exploitation of tools designed for securing connections demands an urgent reassessment of security architectures and the implementation of measures capable of detecting and countering such fileless and self-propagating threats.
By promptly detecting attacks as they occur, AI EdgeLabs stays ahead of the curve, safeguarding your network with proactive threat detection and response leveraging AI capabilities.