In the past, extensive botnet attacks relied significantly on IoT edge devices as the primary means to execute their disruptive attacks on targeted systems. These attacks exploited the inherent vulnerabilities and lack of robust security measures in the IoT devices, making them susceptible entry points for botnet infiltration. Consequently, such attacks frequently caused widespread impact, compromising thousands of devices connected within the network.
With the evolution of the cyber threat landscape, a new generation of botnets has emerged, reshaping the dynamics of attacks. This generation of botnets embraces a different approach, leveraging smaller yet considerably more powerful IoT edge devices. By compromising these vulnerabilities within the IoT edge devices, hackers gain the ability to orchestrate high-volume attacks, redefining the scale and impact of their malicious activities.
CloudFlare reported a DDoS attack in the first quarter of 2023, specifically targeting a telecommunication provider in South America. This attack reached a massive scale of 1.3 terabits per second, which lasted only one minute. The attacker utilized multiple vectors, combining DNS and UDP attack traffic. This particular attack was part of a larger campaign involving several Terabit-strong attacks originating from a Mirai-variant botnet that compromised 20,000 devices.
Effective edge security solutions play a crucial role in actively defending against ongoing cyberattacks, making many of these botnets ineffective. These security measures prevent widespread disruptions to critical systems by proactively mitigating volumetric attacks. According to the European Union Agency for Cybersecurity Threat Landscape Report of 2022, the Mirai botnet alone has been attributed to a staggering number of attacks on IoT devices, exceeding 7 million incidents.
How do botnets work?
A botnet is a group of connected devices, such as Internet of Things (IoT) hardware systems, that are all simultaneously used to overwhelm targeted servers by flooding them with requests to deplete the server resources.
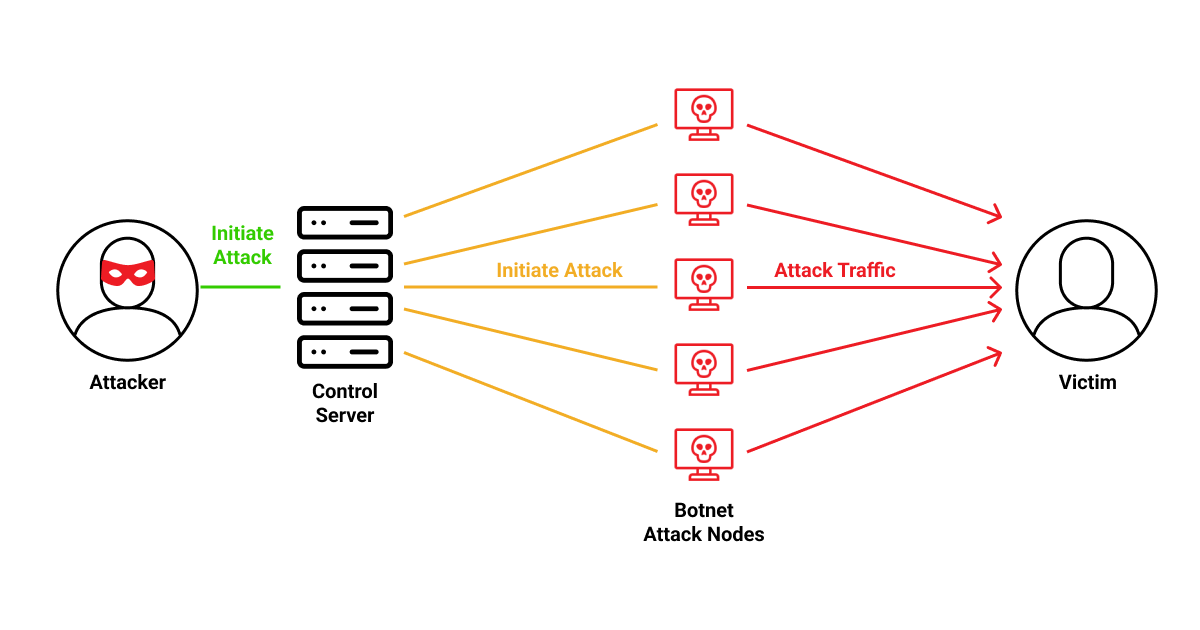
Botnet attacks are normally controlled from a centralized place where the bot headers can continuously update the bots (software applications programmed to execute specific tasks) to change their functionality and adapt to changes in the target system. The hacker can also use these zombie edge devices to carry out more cyber attacks as it leverages the communication channel of the infected computer. This allows the hacker to reach more devices, adapt to changes, and deliver software updates to the bot device.
Especially in the energy and manufacturing industries, the security approaches focus on the physical layer, including devices such as sensors and cameras that are physically located within the factor. By ensuring the security of this layer, data leakage and unauthorized access to the system can be prevented. One of the most serious cyber attacks on smart factories are botnets with distributed denial of services (DDoS) capabilities, as it takes control of a group of internet-connected devices leading to financial losses and system downtime.
To understand the history of botnets, it is important to examine the developments of DDoS attacks. One particular type of attack that has had a significant impact on systems is known as a volumetric attack. These types of attacks involve flooding a target’s server with an enormous amount of traffic, making it difficult or impossible for legitimate traffic to get through. The goal of such attacks is to disrupt the targeted services and prevent legitimate traffic from reaching its intended destination.
Remote programming is used to control all botnet attacks, with command and control (C2C) servers as the sources of all instructions. Commands can be delivered directly or indirectly to the devices, utilizing both client-server and decentralized peer-to-peer models.
In a centralized model of command delivery to zombie devices, a single server acts as a control and command center. This eliminates the need for the bot header to individually manage each device on the network, as they can instead issue commands simultaneously through a centralized server.
A P2P network is also being used by botnets, which involves a network of infected devices. For a hacker to create a P2P botnet, they must first gain control of users’ devices. These types of attacks are challenging to defend against, as the security teams must clean all of the zombie devices in the network. The P2P model connects every device to one another without requiring a central server, making it more difficult to contain and eradicate. Due to this reason, there has been an increase in the number of P2P IoT botnet malware families.
Security solutions against botnet attacks on IoT edge devices
We have designed the AI EdgeLabs security solution with the aim of securing the distributed edge infrastructure that has become a backbone for digital transformation. With the introduction of AI, cyber-attacks have become more sophisticated and backbreaking for a traditional cybersecurity approach to mitigate them. AI EdgeLabs has been built for edge and connected IoT devices to protect them from any threat in real time.
AI/ML for Incident Detection and Response
Our security approach uses pre-trained machine learning models that can automatically adjust and optimize their behavior in response to changes in the underlying infrastructure or network topologies. For example, if the network undergoes changes in traffic patterns, a self-adaptive security system will automatically adjust its settings and configuration to ensure that it continues to function optimally.
The self-adaptive approach is beneficial for edge environments, susceptible to botnet attacks, as it can change the network topology as well as there can be changes in the traffic pattern. This ability will enable the system to be flexible and responsive to changes while minimizing the risk of errors and optimizing network performance.
Improved visibility to the endpoints
Advanced network visibility into endpoint devices is a critical aspect of AI EdgeLabs' security solution in the battle against IoT botnet attacks. This advanced capability provides real-time network visibility, enabling security teams to continuously monitor and analyze the network infrastructure. By leveraging this valuable network data, organizations can actively identify and respond to potential threats, ensuring prompt mitigation measures.
Another ability of our security platform is a centralized dashboard, which provides a comprehensive view of the entire network. The dashboard shows attack surface visibility, allowing internal security teams to identify vulnerabilities and weak points in the network. It provides valuable insights into the network topology, signaling any abnormal behavior or suspicious activities that may indicate an ongoing botnet attack.
IP blocking and IPS
The EdgeLabs Sensor is specifically designed to identify and prevent various cyber attacks, including DoS/DDoS and Botnet attacks, among others. Utilizing container-based technology and AI models, this advanced application offers enhanced threat detection capabilities, resulting in improved accuracy and rapid response times.
Similar to an IPS system, it generates alerts and initiates automated actions, such as the blocking of suspicious IP addresses and the isolation of compromised devices. Our IP blocking and filtering technique effectively accomplishes these tasks as well.
In mission-critical applications, it is important to address the presence of compromised IoT edge devices effectively. The potential of botnet attacks to exploit these compromised devices and infect others within the network can lead to significant consequences. To mitigate this risk, our security solution provides an IP blocking feature. This technique allows the system to selectively block specific IP addresses associated with compromised IoT edge devices, effectively isolating them from the network. By implementing this measure, we ensure the security of other deployed devices while containing and neutralizing the threat posed by the compromised device.
Conclusion
Industry reports suggest that DDoS attacks are moving towards mobile networks and IoT edge devices as they have limited resources and often lack security protections. With the increasing complexity of the edge ecosystem and distributed resources, DDoS attacks are commonly seen to disrupt the operation of these devices.
Industry experts believe Mirai-based botnets remain a primary threat for 2023 in the IoT space as their operators actively manage these malicious networks, which frequently update the long list of misused old vulnerabilities with new exploits that can further help them expand their size.
In the next article, we will focus on additional instances of IoT botnet attacks from the past. It will provide an extensive analysis of several capabilities of AI EdgeLabs, such as the use of reinforcement learning algorithms for identifying abnormal traffic patterns, threat modeling, endpoint detection and response and extended detection and response, and monitoring operating system telemetry data. All of these capabilities will assist organizations in fighting against these attacks.



