Authors:
Serhiy Protsenko, Chief Artificial Intelligence Officer, AI EdgeLabs
Marko Zbirka, Cyber Security Researcher, AI EdgeLabs
Understanding Ebury Malware
Ebury is a sophisticated malware family targeting Linux servers. It primarily functions as an OpenSSH backdoor and credential stealer, compromising nearly 400,000 servers worldwide over the last years. Ebury malware is exceptionally dangerous for Linux servers due to its ability to persistently infiltrate systems, exfiltrate sensitive data, and evade detection by system administrators. It utilizes various propagation methods such as credential stuffing, exploiting vulnerabilities, and adversary-in-the-middle attacks to maximize its reach.
The Ebury malware infiltrates systems by modifying critical components like the libkeyutils.so.1 library to include its payload. It exfiltrated data by hooking into functions used by the libcurl library, enabling it to capture HTTP POST requests and relay sensitive information to its operators. This malware is particularly adept at hiding its presence, making it a formidable threat to any Linux-based environment.
Detailed Analysis and Threat to Modern Linux Infrastructure
Persistent Infiltration:
- Library Modification: Ebury modifies the libkeyutils.so.1 library to include its payload, ensuring its persistence on the infected system. This modification allows Ebury to be loaded by other applications that use this library, such as OpenSSH and libcurl, thus spreading its reach within the system.
- Advanced Hooking Mechanisms: By hooking into functions of the libcurl library, Ebury can capture sensitive data from HTTP POST requests, including credentials and other personal information. This data is then relayed back to its operators, compromising the integrity and confidentiality of the affected system.
Data Exfiltration:
- Credential Theft: Ebury is designed to steal credentials by logging keystrokes and capturing password files. It targets SSH credentials specifically, which are crucial for administrative access to servers. This capability allows attackers to gain unauthorized access to other systems and networks, facilitating lateral movement within an organization’s infrastructure.
- Automated Data Collection: Ebury periodically collects data, including SSH private keys, known_hosts files, and lists of running services. This automated collection of sensitive information enhances its effectiveness in exfiltrating critical data without raising immediate suspicion.
Evading Detection:
- Log Manipulation: Ebury operators remove log entries that indicate their activities, such as new session creations from their IP addresses. By tampering with log files, Ebury effectively hides its presence from system administrators and security tools that rely on log analysis for intrusion detection.
- Rootkit Capabilities: Ebury functions as a userland rootkit, masking its activities and processes within the system. This makes it difficult to detect using traditional security measures, as it can hide its presence from system monitoring tools.
Propagation Methods:
- Credential Stuffing: Ebury spreads by using stolen credentials to gain access to other systems. This method is highly effective in environments where password reuse is common, allowing the malware to infect multiple systems within a network quickly.
- Exploiting Vulnerabilities: Ebury exploits known vulnerabilities like Dirty COW (CVE-2016-5195) to gain root privileges on compromised servers. This allows the malware to perform actions that require administrative rights, further embedding itself within the infrastructure.
- Adversary-in-the-Middle Attacks: By intercepting and modifying legitimate network traffic, Ebury can inject its payload into systems without direct access. This propagation method increases its reach and effectiveness, particularly in environments with robust perimeter defenses.
Impact on Modern Linux Infrastructure:
- Operational Disruption: The presence of Ebury can lead to significant operational disruptions. By compromising critical components and stealing administrative credentials, the malware can affect the normal functioning of servers, leading to downtime and loss of productivity.
- Data Breaches: The exfiltration of sensitive data, including personal information and credentials, can result in severe data breaches. This not only affects the organization’s reputation but also has legal and financial implications.
- Security Degradation: Ebury’s ability to evade detection and manipulate logs degrades the overall security posture of the affected infrastructure. Traditional security measures become less effective, necessitating advanced detection and response capabilities to mitigate the threat.
Ebury malware represents a significant threat to modern Linux infrastructure due to its sophisticated mechanisms for persistence, data exfiltration, and evasion. Effective detection and mitigation require advanced cybersecurity solutions like AI EdgeLabs, which leverage machine learning, behavioral monitoring, and comprehensive EDR capabilities to safeguard systems against such complex threats.
Detecting Ebury Malware with AI EdgeLabs: Technical details
AI EdgeLabs excels in detecting, blocking and mitigating Ebury malware through its advanced Endpoint Detection and Response (EDR) capabilities. Here's a detailed look at how AI EdgeLabs can identify the specific actions and parameters associated with Ebury malware:
1. Credential Access Patterns:
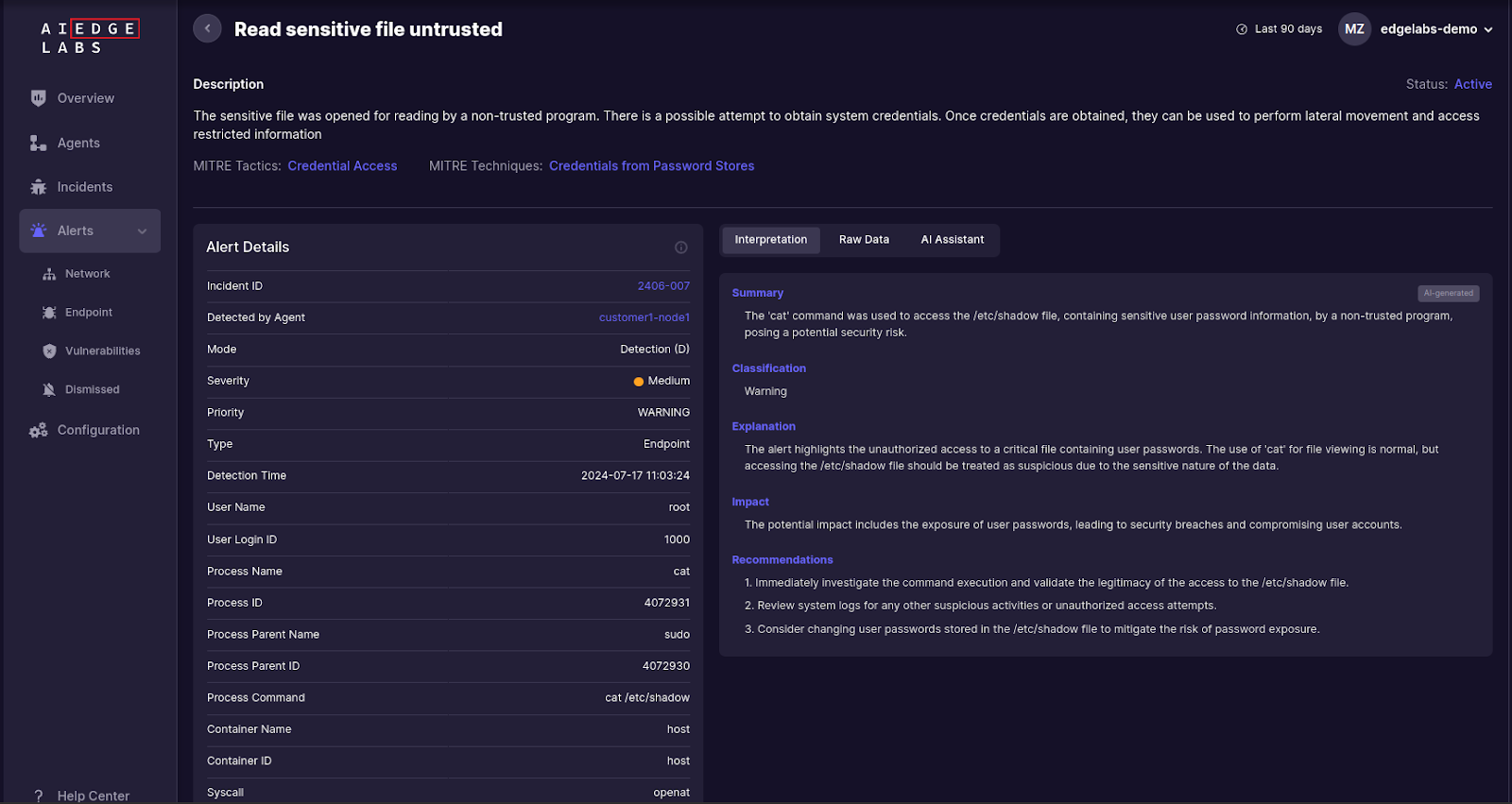
Ebury attempts to read sensitive files like /etc/shadow to obtain system credentials. AI EdgeLabs can detect when a non-trusted program tries to access these files, generating alerts with details such as the process ID, user ID, and the exact file accessed.
Detection Marker: Monitoring access to sensitive files like /etc/shadow by untrusted programs.
Relevant AI EdgeLabs Pattern:
- Read Sensitive File Untrusted: This pattern detects when a sensitive file is opened for reading by a non-trusted program, indicating an attempt to obtain system credentials.
Ebury uses commands like grep and find to search for credential files. AI EdgeLabs monitors these commands, flagging searches targeting locations like /home directories, /etc, and other common places where credentials might be stored.
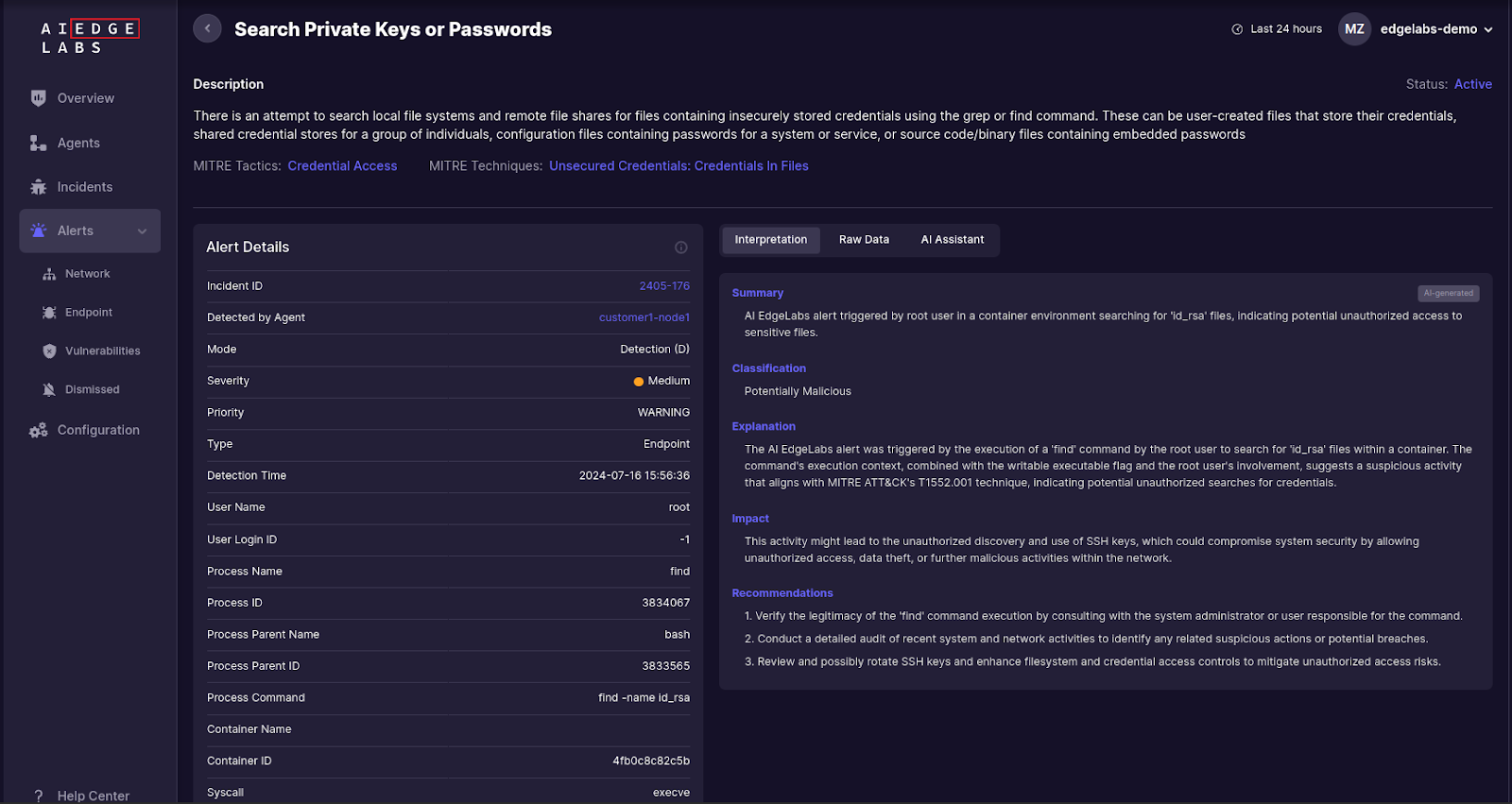
Detection Marker: Monitoring for the use of grep and find commands targeting credential files.
Relevant AI EdgeLabs Pattern:
- Search Private Keys or Passwords: This pattern detects the use of commands like grep or find to search local file systems and remote file shares for files containing insecurely stored credentials.
2. Privilege Escalation Patterns:
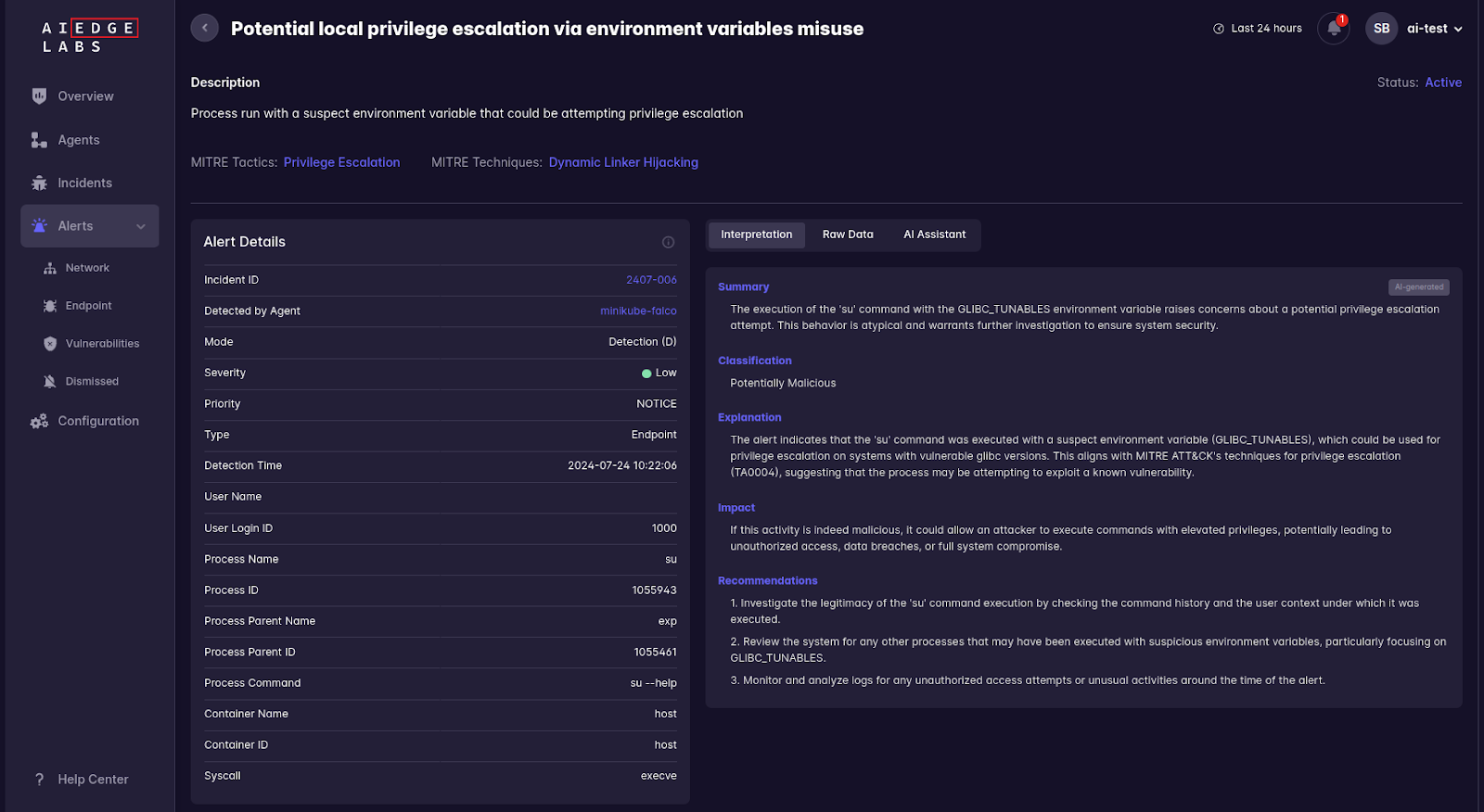
Ebury malware utilizes methods that involve misconfigurations or abuses of sudo settings, allowing users to execute commands with elevated privileges without proper authorization.
Detection Marker: Monitoring unauthorized sudo attempts by unprivileged users.
Relevant AI Edgelabs Patterns:
- Potential Local Privilege Escalation via Environment Variables Misuse: This pattern can detect attempts to gain unauthorized access or escalate privileges by exploiting environment variable settings.
- Sudo Potential Privilege Escalation: Detects unauthorized sudo attempts by unprivileged users, which Ebury might use to escalate privileges.
3. Execution Patterns:
Shared Modules: Ebury malware operates by hooking the keyutils shared library, which is loaded by OpenSSH and libcurl. AI EdgeLabs can detect the loading of these modified shared libraries, identifying the processes involved and the suspicious modifications. A common method used by Ebury involves dropping a malicious libkeyutils.so file next to the legitimate one and modifying the symbolic link to point to the malicious file.
Detection Marker: Monitoring the loading of shared libraries and identifying modifications to critical system libraries.
Relevant EDR Pattern:
- Modify Shell Configuration File: Suspicious attempts to modify shell configuration files to establish persistence.
- Drop and Execute New Binary in Container: Detects execution of binaries not belonging to the base image of a container, indicating modification or injection.
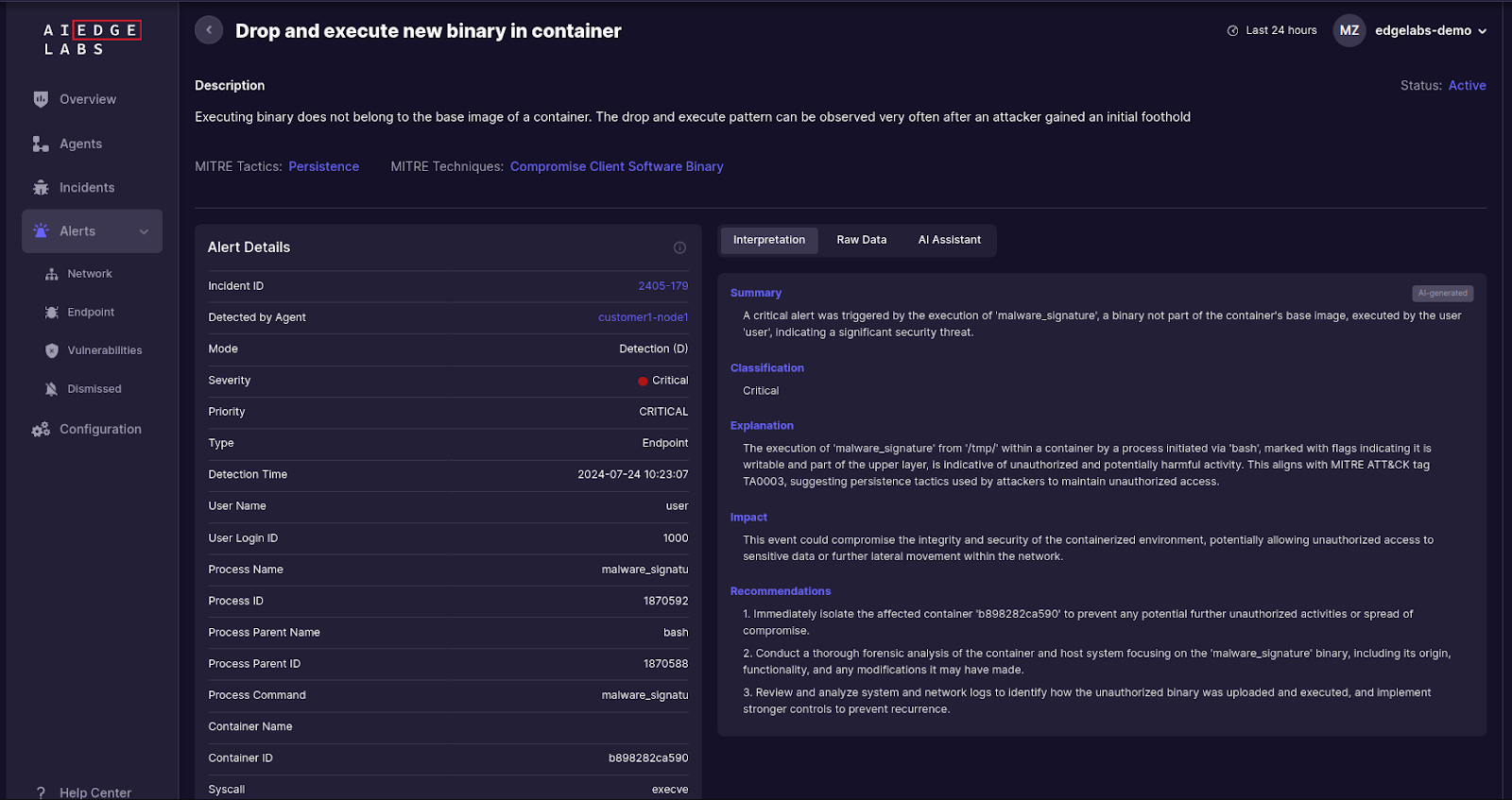
4. Persistence Patterns:
Compromise Client Software Binary: Ebury modifies the keyutils library to introduce malicious behavior into the OpenSSH client and the curl library. AI EdgeLabs can detect changes to critical system libraries, logging the modification details and alerting on the processes involved. This allows for the identification of unauthorized modifications to the keyutils library that affect the OpenSSH client and the curl library.
Detection Marker: Detecting modifications to client software binaries and logging details of changes to critical system libraries.
Relevant EDR Pattern:
- Modify Shell Configuration File: Suspicious attempts to modify shell configuration files.
- Drop and Execute New Binary in Container: Execution of a binary not part of the base container image, suggesting modification or addition.
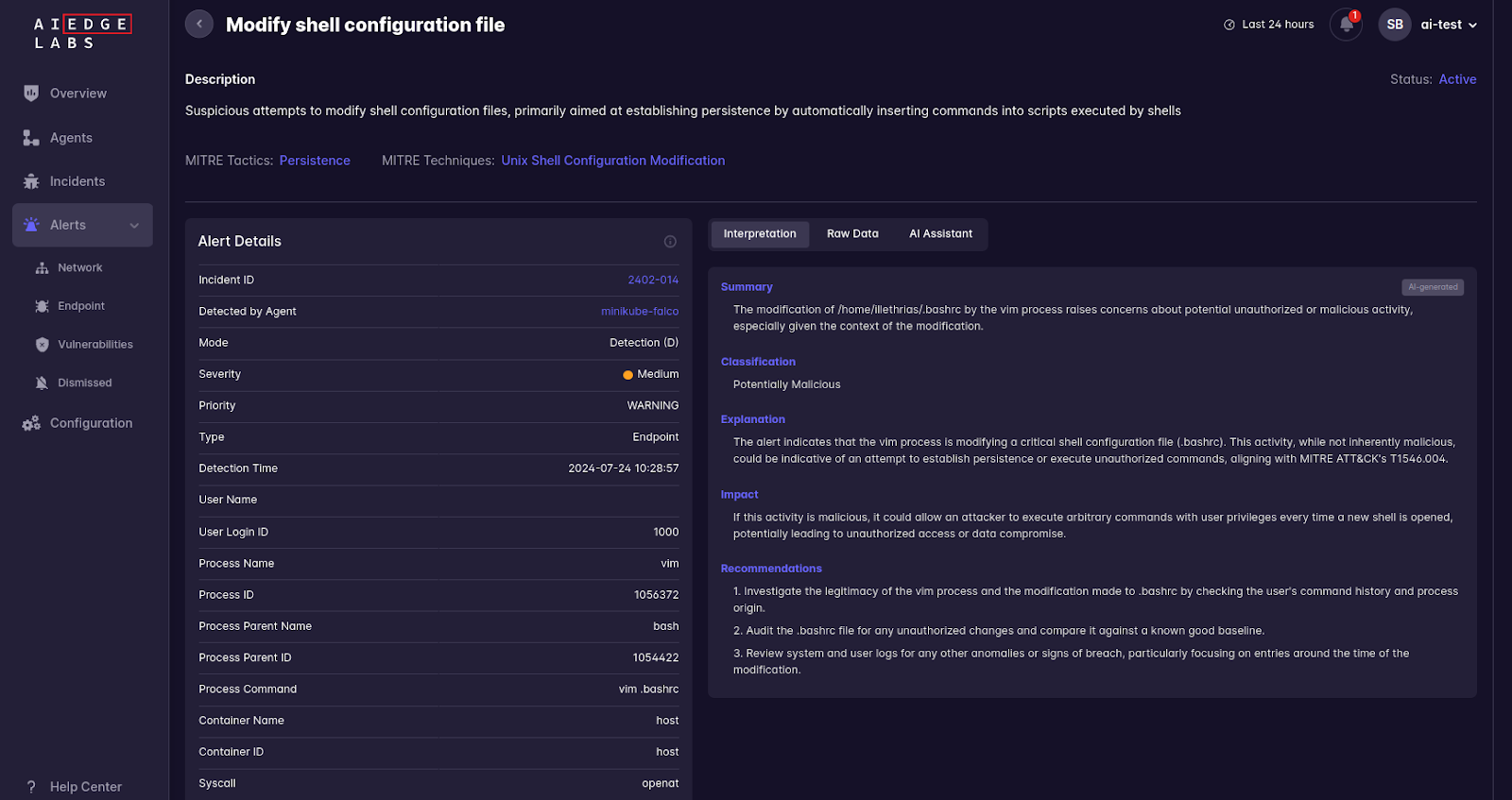
Hijack Execution Flow: Ebury uses the LD_PRELOAD environment variable to inject itself into programs launched by SSH sessions. AI EdgeLabs monitors environment variable manipulations and detects suspicious injection attempts, providing details on the involved processes and environment settings.
Detection Marker: Monitoring changes to environment variables, particularly LD_PRELOAD, to detect injection attempts.
Relevant EDR Pattern:
- Potential Local Privilege Escalation via Environment Variables Misuse: Detects suspicious environment variable settings used for privilege escalation.
- PTRACE Attached to Process: Detects attempts to inject code using PTRACE, which can be related to manipulating execution flow.
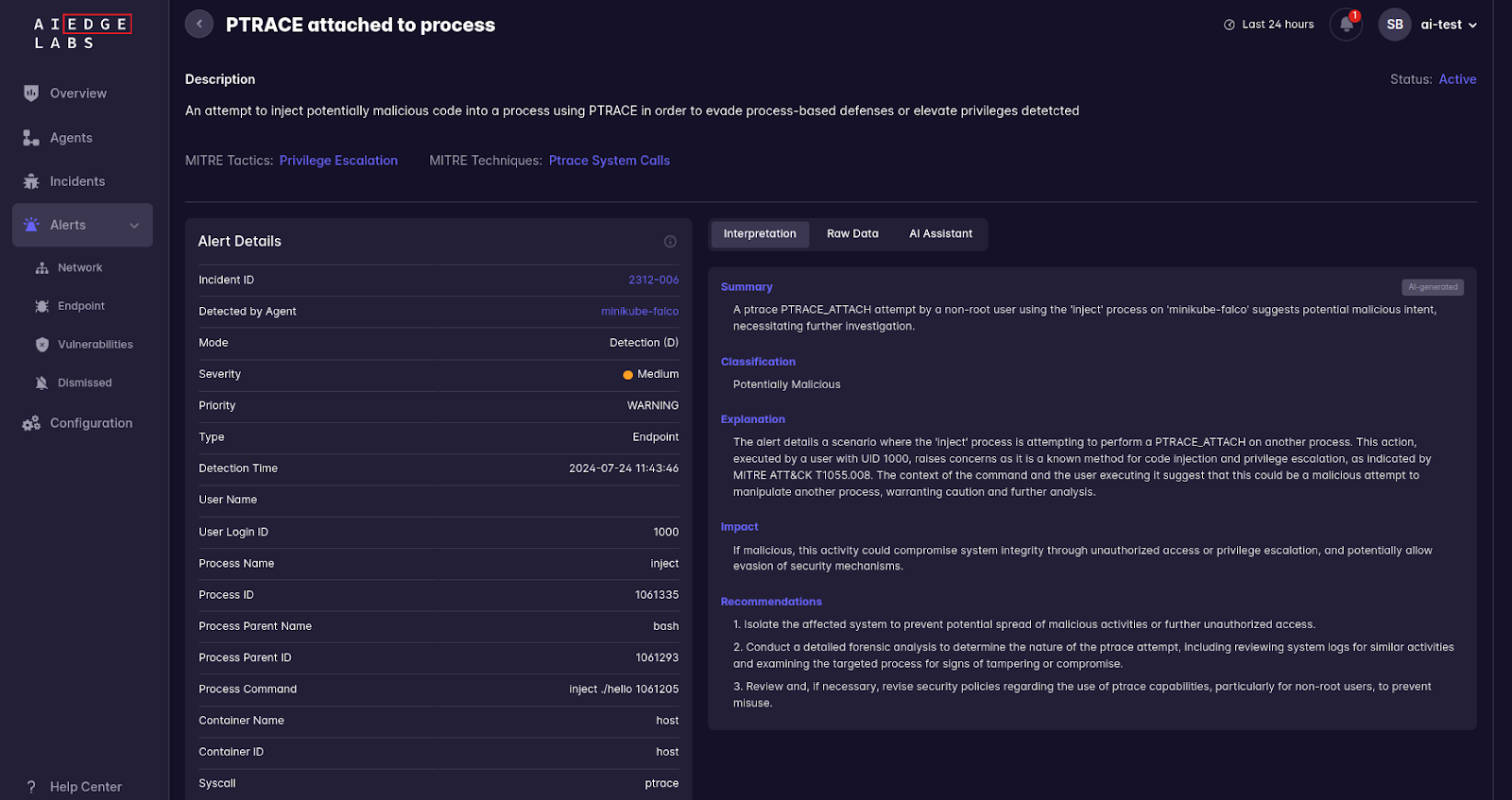
5. Defense Evasion Patterns:
Clear Log Activities: Ebury clears system logs to hide its activities. AI EdgeLabs monitors log files for unusual deletions or truncations, alerting on specific log files affected, the process performing the action, and the time of the event.
Detection Marker: Monitoring log files for unusual deletions or truncations, alerting on specific log files affected, the process performing the action, and the time of the event.
Relevant EDR Pattern:
- Clear Log Activities: Specifically detects the clearing of critical access log files.
- Delete or Rename Shell History: Detects attempts to delete or rename shell history files to remove evidence.
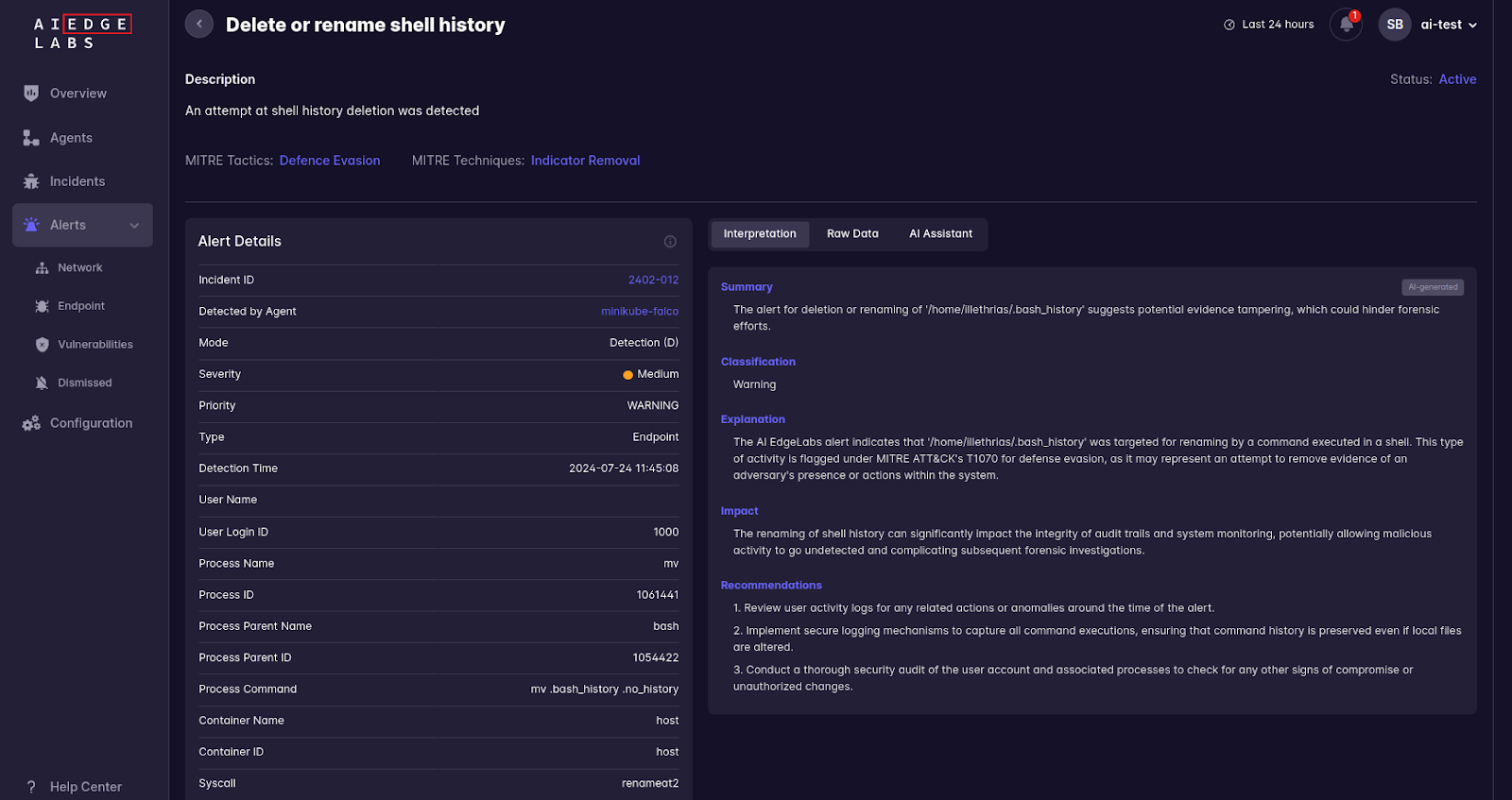
Rootkit: Ebury acts as a userland rootkit when injected inside the shell of SSH sessions. AI EdgeLabs can detect the presence of rootkits by monitoring for known rootkit behaviors and scanning for hidden processes and files.
Detection Marker: Detecting rootkit behaviors and scanning for hidden processes and files.
Relevant EDR Pattern:
- PTRACE Anti-Debug Attempt: Detects attempts to avoid debuggers, which can be associated with rootkit behaviors.
- Fileless Execution via memfd_create: Detects fileless execution techniques that avoid leaving disk artifacts.
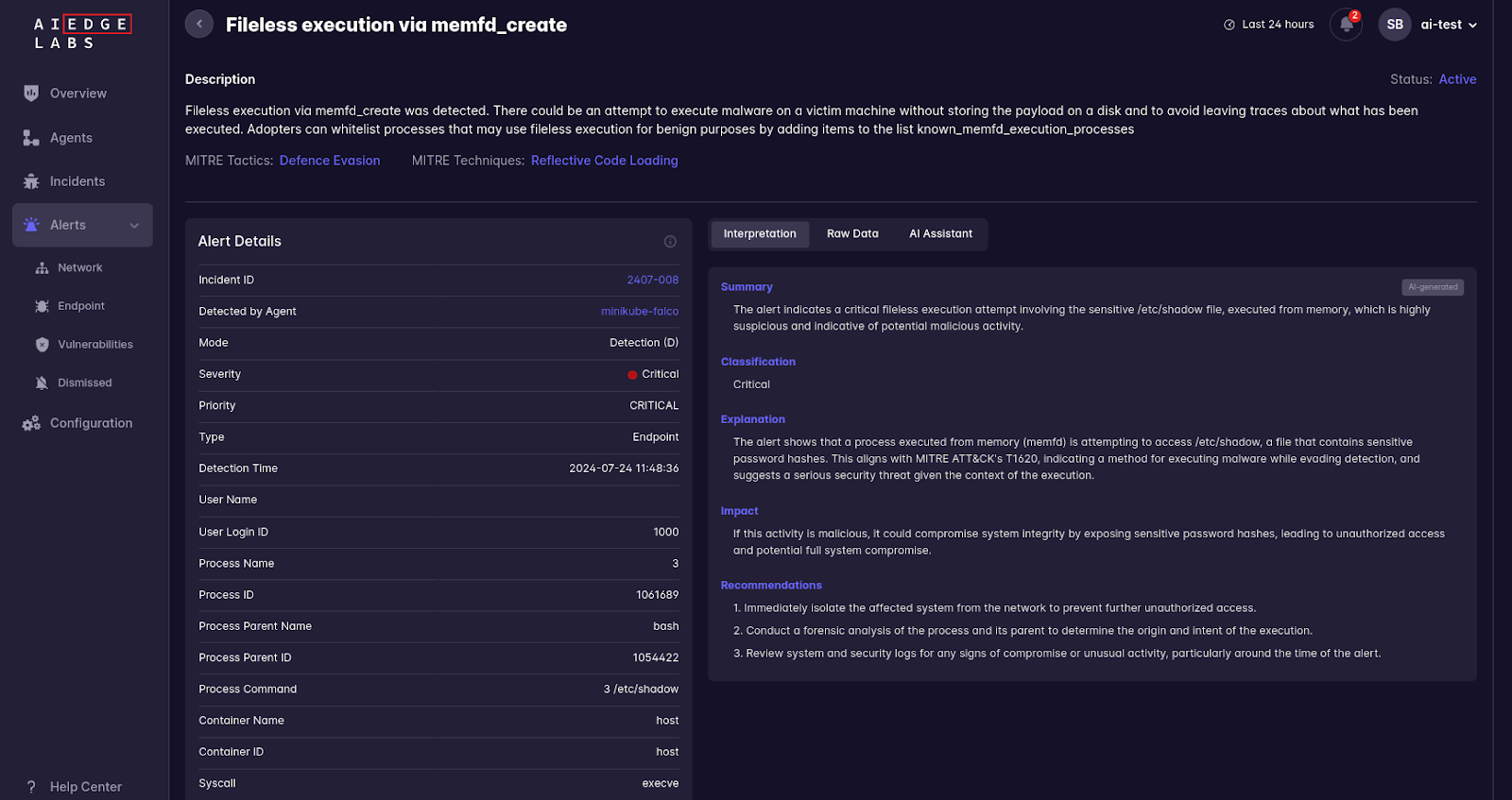
6. Network Activity Monitoring:
Malicious DNS Requests: AI EdgeLabs includes a robust module for detecting malicious DNS activity. Ebury communicates with command-and-control servers using domains such as qimpj6kkofzf.biz, op3f1libgh.biz, larfj7g1vaz3y.net, pbarsec.com, and checklicence.net. AI EdgeLabs monitors DNS requests and flags any attempts to resolve these malicious domains, providing details on the requesting process and destination IPs.
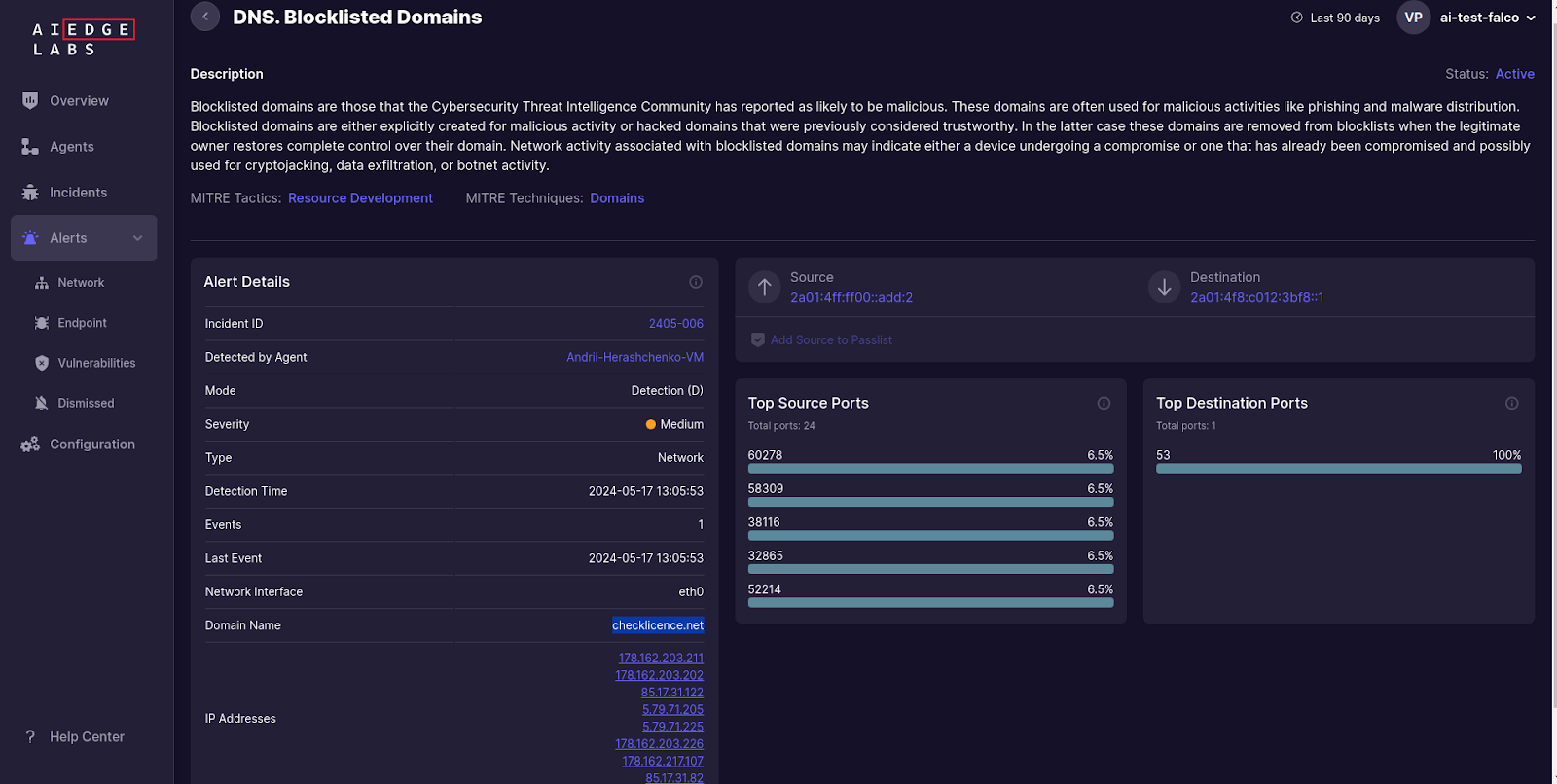
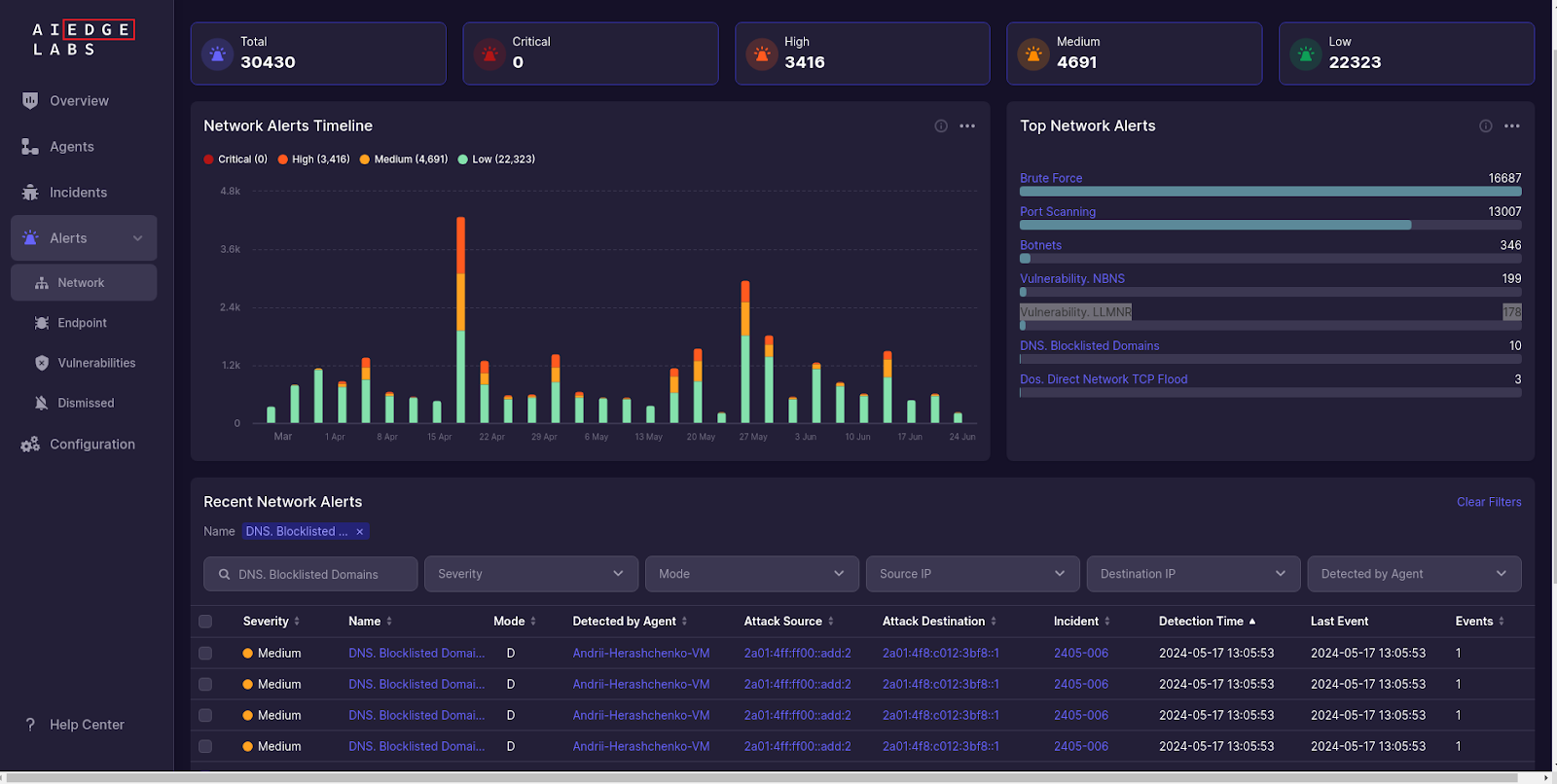
By monitoring DNS requests, AI EdgeLabs can prevent data exfiltration and command-and-control communication, crucial for mitigating the impact of Ebury infections.
7. Signature detection
Malware signature detection: AI EdgeLabs utilize industry standard engine for rule-based detections of malicious files in the system. Thanks to extensive research of Ebury malware by the cybersecurity community we have a sizable list of IOCs (Indicators of compromise) and signature rules. Such as the known file hash: 0a4d7321a74e7c86ad017f99d62899cebbf66752955a64cb36e6b19191d6c09c. AI EdgeLabs continuously scans new and modified files on the system for the presence of known signatures and provides detection and automatic prevention before such files can be used for the attack.
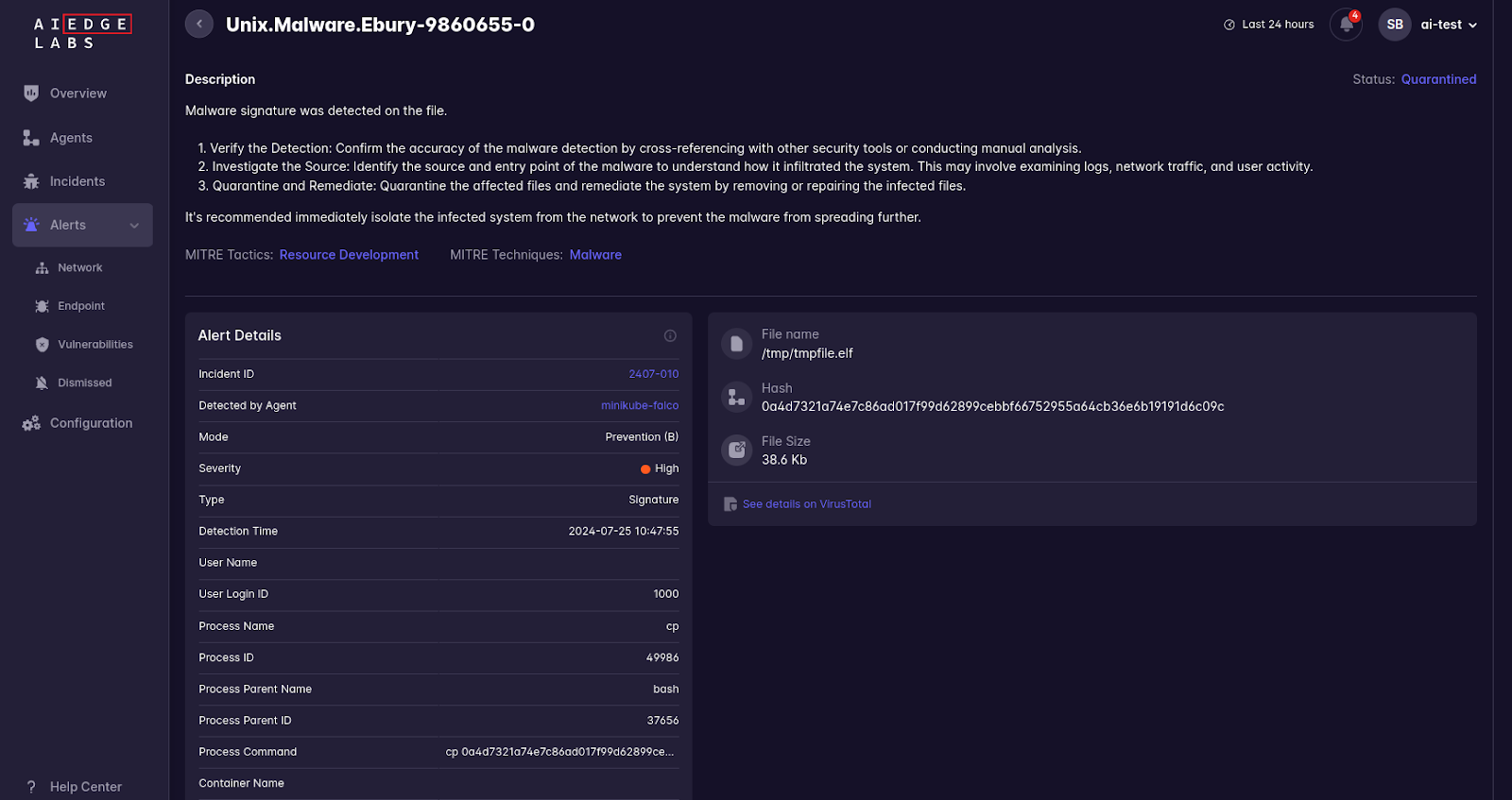
Why AI EdgeLabs is Efficient for Linux Security
AI EdgeLabs is a cutting-edge cybersecurity solution designed to protect Linux servers, cloud instances, Kubernetes, and Docker containers. Leveraging advanced machine learning and behavioral monitoring, AI EdgeLabs provides real-time threat detection, blocking, and comprehensive runtime security. Here’s why AI EdgeLabs is a highly effective solution for detecting and blocking sophisticated malware like Ebury:
Comprehensive Monitoring and Detection
Linux Servers & Cloud Instances:
- Kernel Event Monitoring: AI EdgeLabs uses custom rules and machine learning models to monitor kernel events. It enhances these events with metadata from various sources, such as container and Kubernetes metadata, to provide instant alerts for unusual behaviors and potential threats. This comprehensive approach ensures that any anomalous activity indicative of malware like Ebury is promptly detected.
- Advanced Behavioral Analysis: By analyzing system behaviors and detecting deviations from normal activity, AI EdgeLabs can identify subtle signs of compromise, such as unauthorized file access, privilege escalation attempts, and the use of uncommon system calls.
Kubernetes & Docker:
- DaemonSet Deployment: AI EdgeLabs is deployed as a DaemonSet in Kubernetes environments, allowing it to monitor system events across all containers in each pod and the underlying host. This guarantees constant surveillance of both host and container workloads without requiring additional sidecars.
- Container-Specific Threat Detection: AI EdgeLabs detects threats specific to container environments, such as attempts to escape from containers, execute unauthorized code, or manipulate data within containers. This is crucial for identifying the tactics used by malware like Ebury.
Lightweight Network Traffic Analysis
- Encrypted Traffic Analysis: AI EdgeLabs can detect attacks in encrypted TLS/SSL traffic without requiring decryption. It uses behavioral machine-learning models to analyze the headers and patterns of encrypted traffic, conserving resources while still effectively identifying malicious activity.
- Efficient Resource Utilization: This lightweight approach ensures that the system resources are not overburdened by deep packet inspection (DPI) and traffic decryption, making AI EdgeLabs a highly efficient solution for real-time threat detection.
Advanced Machine Learning and EDR Capabilities
Real-Time Threat Detection:
- Machine Learning Models: AI EdgeLabs leverages advanced machine learning techniques to analyze network traffic and system calls. It can identify known and unknown attacks by converting them into feature vectors and graph structures.
Endpoint Detection and Response (EDR):
- eBPF System Call Analysis: AI EdgeLabs uses eBPF (extended Berkeley Packet Filter) to monitor system calls and identify malicious activities. This low-level monitoring capability is crucial for detecting actions like unauthorized file access, privilege escalation attempts, and other behaviors associated with Ebury malware.
- Detailed Threat Patterns: AI EdgeLabs categorizes threats into several groups, including Credential Access, Execution, Privilege Escalation, Persistence, and Defense Evasion. By using detailed threat patterns, AI EdgeLabs can detect specific actions associated with Ebury, such as the exploitation of Dirty COW for privilege escalation or the use of the LD_PRELOAD environment variable for injecting malicious code.
DNS Activity Monitoring:
- Malicious DNS Requests: AI EdgeLabs includes a robust module for detecting malicious DNS activity. It can identify and block domains used by malware like Ebury, preventing data exfiltration and command-and-control communication.
- Comprehensive Network Monitoring: By monitoring DNS requests and other network activities, AI EdgeLabs ensures that any attempts to communicate with malicious domains are promptly detected and mitigated.
By integrating these advanced capabilities, AI EdgeLabs offers unparalleled protection against sophisticated threats like Ebury malware, ensuring the security and integrity of your Linux servers, cloud instances, and containerized environments.
Conclusion
AI EdgeLabs provides robust and comprehensive protection against Ebury malware, leveraging advanced EDR patterns and DNS detection capabilities. By detecting and blocking both EDR patterns and DNS activity, AI EdgeLabs ensures that your Linux servers and containerized environments remain secure from sophisticated threats like Ebury malware. Invest in AI EdgeLabs to stay ahead of evolving cyber threats and protect your critical infrastructure effectively