For years, cybersecurity regulations lagged behind innovation. Companies built faster, smarter, more distributed systems, but regulators were slow to respond. But that era is over.
With the EU’s NIS2 Directive and Cyber Resilience Act (CRA), the rules of engagement have fundamentally changed. Security is no longer a matter of best practice, it’s a legal, operational, and competitive necessity, especially right now when the whole geopolitical situation globally is changed and the security of each individual organization becomes a matter of national security. And nowhere is this shift more disruptive than at the edge, where AI, data, and critical infrastructure converge, which are widely targeted not only by money-driven cyber adversary groups or individual criminals, but nation-wide cyber criminal groups who do not seek recognition or blackmail for ransomware pay-out, their goals are very far from that. The EU government understands that and deliberately changes the rules of the game.
Recent Incidents That Changed the Conversation
If anyone still doubts that cyber incidents ripple far beyond the company that gets hit, the last few months delivered a harsh reality check. Modern infrastructure is deeply interconnected, and a single compromised node can trigger disruption across entire sectors, regions, and supply chains. Two recent events illustrate exactly why NIS2 and CRA are arriving not a moment too soon.
1.The Collins Aerospace Incident
In September 2025, a ransomware attack targeting a third-party provider disrupted airport operations across Europe. Collins Aerospace, whose MUSE system powers automated check-in kiosks and baggage drops, became the unexpected chokepoint. A Russian-speaking group called Everest claimed responsibility, though attribution remains unverified. What isn’t in doubt is the impact. Airports in Berlin, Brussels, and Heathrow felt the shock immediately. Dublin and Cork followed through cascading effects. Digital procedures fell back to manual operations, creating queues, delays, and cancellations. The breach didn’t stay at Collins; it propagated through the aviation ecosystem and temporarily rewired how critical infrastructure functioned. This is exactly the type of scenario NIS2 is meant to prevent: a single weak link disrupting multiple essential services across borders causing national security incident events.

Representation image of passengers waiting at Heathrow Airport, London (Reuters: Isabel Infantes)
2. The Jaguar Land Rover Shutdown
Just weeks earlier, the UK experienced what has been called the most damaging cyberattack in its history. On August 31, a coordinated attack forced Jaguar Land Rover to shut down its entire IT infrastructure. Production lines went silent until early October. The financial fallout was severe, part of a reported £485 million loss for the period, but the broader consequences were even more telling. JLR’s supply chain, heavily reliant on just-in-time delivery, was thrown into chaos. Many small and midsize suppliers lost their primary customer overnight and were pushed to the edge of bankruptcy. Three well-known English-speaking groups: Scattered Spider, Lapsus$, and ShinyHunters jointly claimed responsibility. These groups are infamous for highly convincing phishing campaigns, and early signs suggest social engineering may have been the initial vector. While the full scope of data exposure remains unclear, leaked screenshots showed internal domains, debugging logs, and even backend source code – a stark reminder of how deeply attackers can penetrate modern development environments.

3. The Ukraine Camera Compromise
In Ukraine, the geopolitical reality has turned cyber risk into a frontline capability, not an IT problem. One of the clearest examples is the growing use of compromised video surveillance as an enabler for real-world operations. In 2025, allied intelligence assessments and open reporting described Russian actors attempting to access border and logistics-area security cameras to track and disrupt the flow of Western aid into Ukraine, turning “ordinary” IP cameras into battlefield reconnaissance. Ukraine has also warned that hostile forces have leveraged access to municipal and commercial CCTV to improve targeting and timing of strikes, effectively using the victim’s own infrastructure as a sensor network. The lesson for CISOs is uncomfortable but direct: in high-pressure environments, like transportation, ICT, video surveillance, edge devices like cameras are not peripheral, they are mission-critical systems. If they’re unmanaged, unpatched, or invisible to monitoring, they become a low-cost entry point with high-impact consequences.

4. Cloudflare’s Signal: AI Attacks at Internet Scale
ʼAI-driven traffic is also reshaping the threat landscape at internet scale and the numbers are no longer abstract. In a recent disclosure, Cloudflare’s CEO Matthew Prince said the company has blocked 416 billion AI bot requests for customers since July 1, 2025. That figure is less about “bots being annoying” and more about what CISOs are seeing inside their own environments: automated scraping, credential stuffing, content theft, and reconnaissance happening continuously, at machine speed, and often indistinguishable from legitimate usage until it’s too late. The message is clear: AI has lowered the cost of attack, increased the volume of probing activity, and compressed response windows. In this environment, resilience depends on controls that can operate continuously, detecting abnormal behavior, enforcing policy, and producing evidence that defenses were active when it mattered.
The Pattern We Can No Longer Ignore
What these incidents demonstrate is not just operational risk, but systemic exposure with national-level consequences. Modern cyber incidents rarely remain confined to a single organization. They propagate through suppliers, service providers, and shared digital infrastructure, often crossing borders and sectors within hours.
This is precisely the risk model underlying both NIS2 and the Cyber Resilience Act. Cybersecurity is no longer treated as an internal corporate concern, but as a matter of economic stability, public safety, and national security. Disruptions affecting airports, manufacturing, transportation, or digital infrastructure are now recognized as capable of escalating into broader societal and economic impact.
NIS2 and CRA formalize this shift in perspective. They embed cybersecurity obligations into critical sectors and product supply chains not to improve individual resilience alone, but to reduce systemic risk at national and EU level. In this context, a single breach is no longer assessed by the size of the affected company, but by its potential to disrupt essential services and interconnected markets.
The Regulatory Wake-Up Call
NIS2 and the Cyber Resilience Act mark a structural change in how the EU governs cybersecurity risk. Rather than issuing guidance or best-practice recommendations, both instruments introduce binding, enforceable obligations tied directly to operational security outcomes, and include policies, security tooling, compliance evidence, and incident reporting & management.
Under NIS2, which entered into force in October 2024, the scope of regulated entities expands significantly to include not only critical infrastructure, but large parts of the manufacturing sector, digital infrastructure providers, telecom operators, cloud and managed service providers, and other organizations whose disruption could have systemic impact. The directive does not prescribe specific technologies, but it mandates continuous risk management, network security and threat detection, supply chain security and active incident detection, and time-bound incident reporting, with initial notifications required within 24 hours of awareness.
Crucially, NIS2 shifts accountability upward. Cybersecurity controls, incident handling, and risk acceptance decisions are explicitly assigned to the organization’s management body. This is not symbolic governance language – executives can be held responsible for inadequate security measures, insufficient oversight, or failure to act on known risks. In practice, this elevates cybersecurity from an operational IT function to a regulated management responsibility, subject to supervisory action and financial penalties.
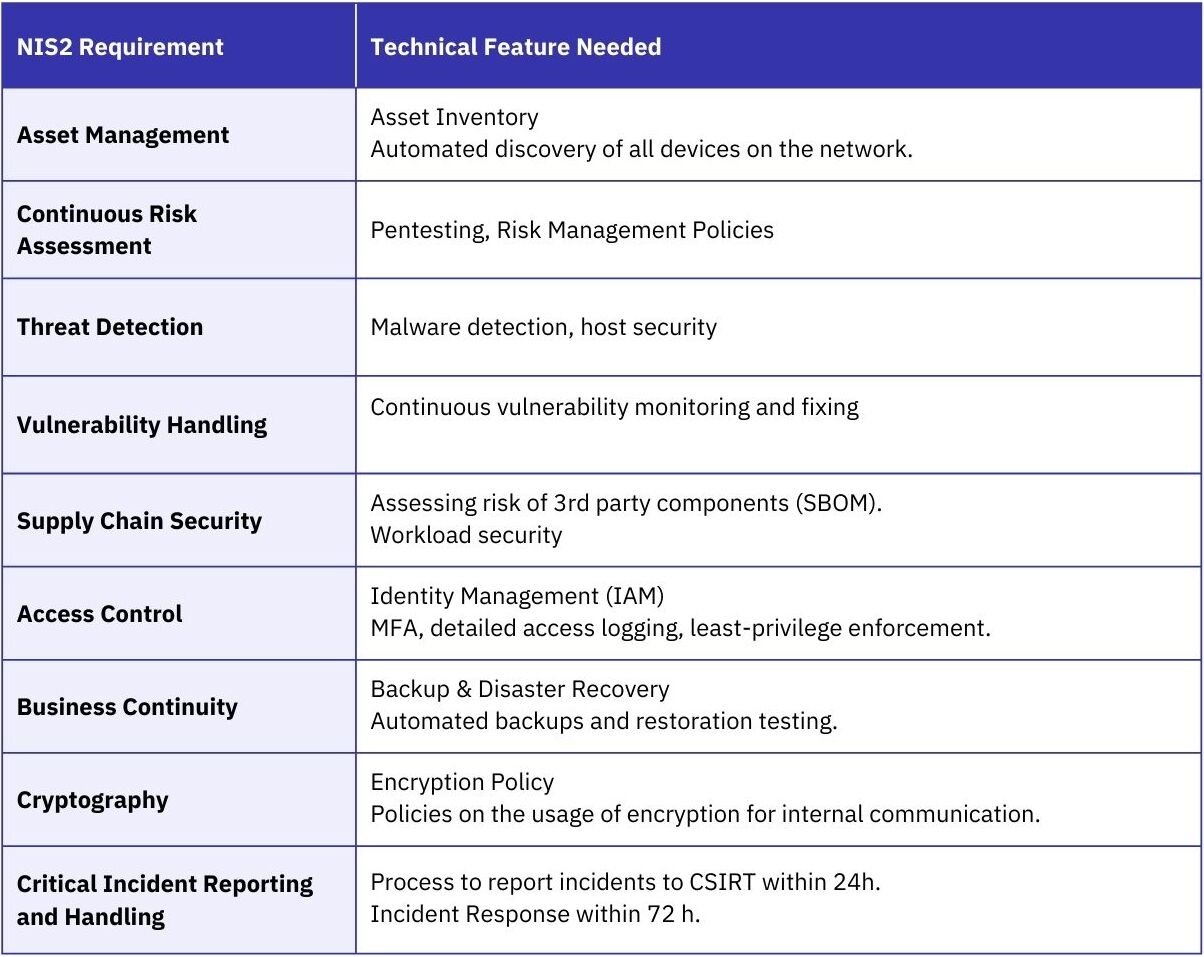
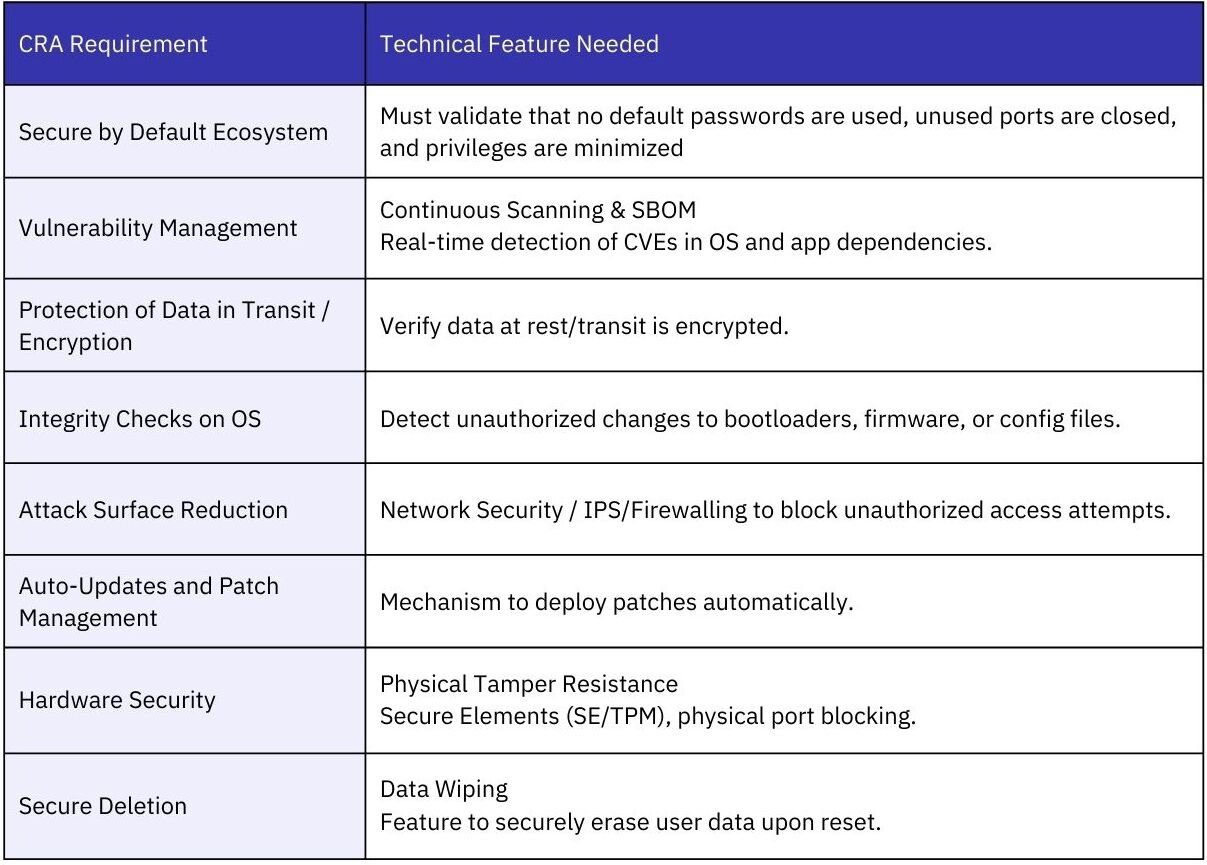
The Cyber Resilience Act applies a similar regulatory logic to the product layer. From 2027, manufacturers of all connected products with digital elements placed on the EU market will be subject to mandatory secure-by-design and secure-by-default requirements. This applies across a broad range of connected products, including industrial controllers, embedded systems, IoT devices, and AI-enabled edge components.
CRA shifts cybersecurity obligations upstream to the vendor. Manufacturers are required to identify and manage vulnerabilities throughout the product lifecycle, provide security updates, and implement coordinated vulnerability disclosure processes. They must also maintain an accurate Software Bill of Materials (SBOM) to document third-party components and dependencies, enabling risk assessment and regulatory oversight. Compliance is assessed not only at the point of market entry, but continuously, with post-market monitoring and enforcement mechanisms tied to demonstrable security maintenance.
“They’re enforceable mandates, carrying fines of up to 2–2.5% of global annual turnover. For context, that’s the same magnitude as GDPR. And just like GDPR reshaped data protection worldwide, NIS2 and CRA are poised to redefine cybersecurity globally”.
What About Distributed Mission-Critical Workloads?
Distributed, mission-critical workloads sit at the core of NIS2’s regulatory scope because they underpin services explicitly classified as essential or important under the directive. Energy, transportation, digital infrastructure, telecom, and certain segments of manufacturing are designated as essential entities due to their direct impact on public safety, economic stability, and national security. Other sectors, including advanced manufacturing, logistics, and smart city operators, fall under important entities, where disruption can still produce significant cascading effects.
Yet these environments are inherently complex and fragmented. Individual nodes may run their own Linux instances, AI models, or Kubernetes clusters; many operate with limited or intermittent connectivity, and most depend on third-party components that evolve faster than traditional patching cycles can accommodate.
A single vulnerability in an edge device can therefore cascade across thousands of endpoints. When such a device also hosts AI workloads, for example, predictive maintenance or computer vision pipelines, attackers may poison data, tamper with models, or hijack GPU resources for cryptomining or lateral movement.
Until recently, this risk was often treated as a by-product of innovation. Under NIS2 and the Cyber Resilience Act, it is now treated as a regulatory and operational liability.
From Voluntary to Mandatory Cyber Resilience
What’s revolutionary about these laws is not that they promote better security – it’s that they eliminate the option of bad security.
NIS2 makes it explicit that organizations must have detection and response capabilities, continuous monitoring, and controlled access across their digital infrastructure, including edge sites. Incident reports can no longer sit buried in SOC queues for days; operators have just 24 hours to notify national authorities of a breach.
Meanwhile, the CRA forces product builders to think like security engineers from day one. Every connected device, every AI controller, every embedded sensor must ship with clear documentation, built-in vulnerability management, and a secure update mechanism that works throughout the product’s lifetime.
Together, they connect both sides of the equation, vendors and operators, into one continuous chain of responsibility. Manufacturers can’t simply ship and forget. Operators can’t assume that security is “someone else’s job.” Both are now accountable for resilience from design to decommissioning.
Compliance Evidence
AI systems complicate compliance because they’re dynamic by nature. Models evolve. Data drifts. Code retrains itself. Traditional “snapshot” certification approaches, once and done, no longer work.
CRA directly challenges this model's opacity. It requires transparency into the digital components of a system, ongoing monitoring, and vulnerability disclosure within 24 hours. In practice, that means organizations deploying AI must maintain traceability: which model version is running, what data it was trained on, and how updates are validated. When combined with NIS2’s real-time incident response obligations, AI systems at the edge must now be auditable, explainable, and secure at runtime – not just during design reviews.
This is forcing a cultural shift inside engineering teams: compliance now requires evidence and continuous reporting.
Supply Chain Transparency Becomes Non-Negotiable
If there’s one word that captures the spirit of both NIS2 and the CRA, it’s accountability – shared, measurable, and enforceable across the supply chain. In modern environments, every connected device and AI system is assembled from a web of third‑party components: firmware, open-source libraries, container images, drivers, and cloud services. Each dependency expands the attack surface, and each supplier relationship becomes part of your risk profile.
The CRA formalizes this reality for vendors by pushing security-by-design obligations into the product lifecycle. Manufacturers are required to maintain an accurate inventory of software components and dependencies, establish vulnerability handling and disclosure processes, and provide security updates throughout the product’s supported lifetime.
For CISOs, the implication is straightforward: supply chain risk is no longer a “procurement problem” or a periodic questionnaire exercise. An unpatched library, an unmanaged edge appliance, or a supplier that cannot evidence its vulnerability management process becomes not just a technical weakness, but a governance and compliance exposure with potential operational disruption, regulatory scrutiny, and material financial impact. The era of treating third‑party security as “out of scope” is over; resilience now depends on proving that your ecosystem is managed, monitored, and maintainable end-to-end.
Real-World Implications
Consider a few scenarios.
A smart manufacturing line uses edge AI for visual quality inspection. The AI controller falls under CRA as a product with digital elements, and the factory itself is an “important entity” under NIS2. If a vulnerability is found in the AI runtime, both the vendor and the operator must act – patch, document, and report, within strict timelines.
Or a telecom provider deploying GPU-accelerated nodes for 5G analytics. Under NIS2, its network functions are critical infrastructure. Any compromised node becomes a reportable incident. If those nodes use third-party AI accelerators, CRA applies to the hardware suppliers too.
Even public transport systems, increasingly reliant on connected ticketing and SCADA control, must now maintain continuous runtime protection and forensic logging – requirements that align directly with NIS2 and CRA’s security-by-design principles.
The takeaway is clear: compliance isn’t confined to data centers anymore. It’s everywhere data lives and moves.
Turning Regulation into Competitive Advantage
The good news? These changes, though demanding, create an enormous opportunity for those ready to adapt fast.
Organizations that embrace NIS2 and CRA early will gain not only legal compliance, but market differentiation. Demonstrating verifiable cyber resilience – auditable logs, AI-assisted runtime defense, automated patching, built-in compliance reporting – becomes a powerful trust signal to customers and regulators alike.
For CISOs, the hard part isn’t buying security tools. It’s proving – quickly and consistently, that controls are operating across edge sites, Kubernetes, IoT gateways, and GPU workloads. Under NIS2 and CRA, “we believe we’re secure” doesn’t survive an audit, an incident, or a customer due diligence call. You need evidence that is continuous, attributable, and exportable.
Below is the implementation model AI EdgeLabs is built around.
Step 1 — Build a complete runtime inventory
Why it matters:
Both NIS2 risk management obligations and CRA product requirements assume clear visibility into what is in scope – systems, workloads, and components.
How AI EdgeLabs helps:
A single lightweight AI agent continuously discovers and secures workloads across hybrid cloud, Linux hosts, edge nodes, Kubernetes clusters, and GPU systems, including what is running and where.
Step 2 — Gather data that stands up in audits
Why it matters:
Auditors and regulators do not accept “the SOC saw something.” They expect logs, timelines, and verifiable control evidence.
How AI EdgeLabs helps:
Via one single AI Agent AI EdgeLabs spans:
- Network and Intrusion defense: packet-level visibility and detections
- Host and Workload security: kernel-level runtime events
- Kubernetes/ container runtime: container activity, drift, and suspicious behavior
- Runtime Vulnerability management: vulnerability monitoring and handling, SBOM monitoring, Linux misconfigurations
Step 3 — Map telemetry to controls
Why it matters:
Raw logs do not answer compliance questions. Control mapping does.
How AI EdgeLabs helps:
The Compliance Center organizes evidence by requirement area, such as incident handling, monitoring, access control, vulnerability handling, and supply chain obligations.
Step 4 — Automate incident reporting and compliance evidence
Why it matters:
NIS2 requires structured reporting and governance; CRA expects documented security posture and vulnerability handling. Manual reporting does not scale.
How AI EdgeLabs helps:
Automated and scheduled reports for:
- executive updates (risk posture, coverage, trends)
- regulator or customer requests (evidence exports)
- incident summaries (timeline and actions taken)
Step 5 — Operationalize response with pre-defined and AI-generated playbooks
Why it matters:
NIS2 is explicit about incident handling and impact minimization. In practice, speed and repeatability are closely scrutinized after an event.
How AI EdgeLabs helps:
AI-generated actionable response playbooks and pre-defined playbooks at the Agent linked directly to detections — defining what to isolate, what to collect, and what to remediate.
What This Really Means
The oversimplified assessment is that NIS2 and CRA compliance requires not only a paper proof now, but a working algorithm and a number of sophisticated security solutions & tools deployed by organization, so it is able not only to monitor its environments and workloads, but proactively report on cyber incidents and response to them to the corresponding authorities and actually bearing legal responsibility in case of failure. In other words, it is not enough to have a bare minimum security level like a perimeter protection only, it is a wake up call to implement sophisticated multi-layered security measures that would actually allow your organization to identify and react to the incident, no matter whether it is a port-scan or an APT multi-layered attack.
So, for CISO who is running extremely distributed environments which include hybrid cloud, datacenters, or/and edge workloads and infrastructure, that would mean the following:
- Security must be extended beyond perimeter protection and asset discovery and management to always-on runtime security across every host, network, and workloads, no matter whether that is a highly connected or airgapped environment.
- Runtime vulnerability monitoring and management; SBOM-monitoring
- Misconfigurations monitoring and fixes
- Continuous risk assessments (pentesting, audits. etc)
- Report on incidents and faster response to the threats and attacks within stated time frames (24 h and 72h).
- Centralized posture management and control-aligned evidence for NIS2 / CRA compliance - reports for authorities, customers, vendors to be able to sell the products and solutions.
The year 2026 should mark the end of this moment of strategic national security uncertainty with NIS2 being widely transposed by all EU member states, and some non-EU states, and demanding sophisticated multi-layered actionable defence from each essential and important enterprise. While CRA is planned to be adopted in 2027, enterprises who sell or manage connected devices and solutions are required to submit a report on existing and exploitable vulnerabilities till September 2026 to gain CES marking and ability to sell and distribute their products in the EU further.
Sources: